Healthcare
Medical Grade Connectivity: How IoT Drives Digital Transformation in Healthcare

The connected world that is enabling the digital transformation of our lives and society is pervasive. So often, people view the radical transitions as dehumanizing – that technology moving us further from each other, making our relationships more distant and our interactions impersonal. However, this really doesn’t hold up to close scrutiny when we consider the context of our whole lives. We’ve never been so connected to people and information – and we are becoming more engaged every day. We are able to stay in touch with family and friends more easily; share experiences even though distant; share intimate ideas over phones even when sitting next to each other. Like so many important areas of our lives, the realization of the connected world is also transforming healthcare. CableLabs hosted an Inform[ED] symposium to investigate how connected healthcare is evolving and what technical challenges it must overcome. Attended by a fantastic mix of technical professionals, visionaries, and subject matter experts, the overwhelming consensus was that emerging technologies and pervasive networking will reinvent healthcare. The result will be an even more humane and caring system, accessible to more and more people at even lower cost.
The connected healthcare event was opened by Simon Kos, Chief Medical Officer of Microsoft. He set the tone for the day, demonstrating how technology is fundamentally changing society as it becomes more accessible, affordable and capable. His view was on our total health – not just during episodic care with clinicians, but our overall quality of life as we cope with the challenges of living. To organize his storytelling, he used the Quadruple Aim framework and presented examples to examine technology innovation along the dimensions of engaging patients, empowering care teams, optimizing clinical and operational effectiveness and transforming the care continuum. His examples resonated with the views and ideas of other presenters and panelists throughout the day.
Transforming Healthcare Through Interoperability and Data Liquidity
Security concerns are very real, as discussed by a panel of Corporate Information Security Officers (CISOs) moderated by Ram Ramadoss of Catholic Health Initiatives. Panelists included Cyrus Malbari of Abbott, Kathy Hughes of Northwell Health, and Timothy Torres of Sutter Health. The rash of ransomware incidents against thousands of hospitals globally demonstrates the severity of the threat environment. Yet, as Mr. Ramadoss discussed with his panel, they can’t control threats. Rather they work to control weaknesses. Some weaknesses are obvious and yet have been very hard to fully mitigate – phishing, being too open with system administrator privileges, exposing sensitive systems to risks by using them for personal activities such as email. Others are not so obvious. Kathy Hughes pointed out that the focus on care tends to decentralize IT – with the result that a large percentage of devices connected to the care network may not even be known to security teams. Timothy Torres said one way his organization found that works to deal with this challenge was to incentivize purchasing devices through correct channels. The panelists all felt that device security certification could be a major improvement in ensuring securable devices were used to provide care. And they cited potential savings in cyber security insurance as a result.
A discussion point that was visited throughout the day was data liquidity. The concept of data liquidity is not synonymous with interoperability, though related. Rather, data liquidity is about ensuring actionable access to health information by whomever needs it. This is a differentiating challenge in healthcare. As Kerry McDermott and Jeff Smith highlighted in the legal and regulatory panel, medical devices are regulated by a plethora of federal agencies. No other industry has the same mix of privacy and security requirements while at the same the ability to produce such rich and valuable data that, applied to the right algorithms and made available to the right person at the right time can save lives while lowering costs.
Fireside Chat with Ed Cantwell
Ed Cantwell and Ed Miller, both from the Center for Medical Interoperability, observed that interoperability and security in connected devices are interdependent. Security functions between devices must be interoperable, and insecure connectivity doesn’t provide practical interoperability. Ed Cantwell went further, describing secure interoperability need to be approached as a utility – a fundamental capability that must exist to support evolving practices in health care. This idea was similar to ideas shared during the IoT Security Inform[ED], where Brian Scriber of CableLabs asserted that code and practices to secure IoT devices and systems should be developed collaboratively and then shared freely.
Ed Cantwell also shared that he thinks blockchain technologies have a role to play here. Blockchains are designed to address trust in a way directly applicable to healthcare, providing a basis for security, privacy, control, transparency, and compliance.
Innovation in Connected Healthcare
The final speakers painted a bright future, discussing in depth how digital transformation will refocus healthcare on the patient, humanizing care. Summer Knight of Firecracker was particularly eloquent, sharing her passion and drive to show how the cable industry can be pivotal in providing medical grade connectivity. She feels that the evolving connectivity will engage and empower individuals and their family as part of the healthcare team as we hardwire humanity at every point of care. Medical grade connectivity can provide the platform for customer engagement and activation, putting the patient in the center of all decisions. The opportunity for contribution from cable is significant. Remote monitoring can reduce costs by as much as $8400/year per patient. Coupled with other critical functions, the near term opportunity for cable operators is over $200 billion annually, supporting a total addressable market of over 170 million people.
This was a very informative event. It brought stakeholders together to chart how we can achieve a bright future in providing secure, connected health. Working together, the cable industry and health care industry can lower the per capital cost of care and we can improve the wellness of populations by making access easier. Medical grade connectivity will improve the patent experience and change how we assess success in providing care as we transition the business focus from fee-for-service to a focus on positive results. We can empower care teams in new ways, ensuring quicker care that allows us to treat patients better and increase the likelihood of excellent outcomes.
Security
The Benefits and Challenges of a Connected World

On April 12, CableLabs hosted an Inform[ED] conference in NYC focused on the emerging IoT security landscape. This open event brought together business leaders, key technologists, and security experts from multiple industry sectors, academia, and government. They shared in-depth views of IoT's evolution and the increasing security, privacy and policy challenges arising from the ongoing and rapidly accelerating deployment of connected devices.
Billions of new devices lead to an increased threatspace
Shawn Henry of Crowdstrike, a retired executive assistant director of the FBI, set the stage for our experts for the rest of the day. His focus and ideas were repeated and supported throughout the event by speakers and panelists. Security threats pose significant challenges to IoT, with real risk to individuals, businesses, and national security. The threats come from terrorist and organized crime groups along with other nation states. New extremist groups such as the Cyber Califate extend activities of terrorists into a cyber Jihad. Organized crime groups focus on theft of personal identifying information they can monetize, targeting capabilities critical to businesses as they evolve extortion.
Criminals target IoT, losing essential data or the ability to use critical devices unless asset owners pay financial compensation to retrieve. A major example is the rash of ransomware targeting hospitals. And, of course, there have been attacks by nation states, notably attributed to North Korea and Iran. All three types of adversaries steal data, change data, and destroy data to achieve their own ends. However, the IoT benefits are worth investment in effort and resources to protect, and IoT security needs to assess the risks posted by bad actors, mitigating vulnerabilities appropriately.
Collaborating on standards and public policy
IoT risk management is also a concern among policymakers, who take notice when insecure devices impact networks and services. Matt Tooley of NCTA discussed with Allan Friedman of the NTIA the agencies' efforts to galvanize all relevant parties toward solutions through a multi-stakeholder process. Gerald Faulhaber of the Wharton School, Chaz Lever of Georgia Tech, and Jason Livingood of Comcast agreed on the need for broadly shared responsibility for IoT security, and Professor Faulhaber noted some form of government oversight may be forthcoming, though the model is unclear. While certification of devices may provide some key elements we need, it's important we understand policy will likely be slow to evolve. This means businesses, including service providers, device manufacturers and others must evolve their security strategies as adversaries evolve their methods of attacking IoT. Industry-driven solutions will continue to provide the most agile responses to new threats.
Threat mitigation
The team of security experts that came together at CableLabs’ Inform[ed] event are working hard to manage risks and mitigate threats. We heard great insights from Dylan Davis of RiskSense, Terry Dunlap of Tactical Network Solutions, James Plouffe of MobileIron and technical consultant to the popular Mr. Robot series, Dan Massey of the DHS Security & Technology directorate, Tobin Richardson from the Zigbee Alliance, and Matt Perry from Microsoft also the OCF Board of Directors President. Service provider experts includes Brian Rexroad of AT&T, Clarke Stevens of Shaw Communications, and Rich Compton of Charter Communications. This fantastic body of experts provided substantive insight into the IoT security challenge and what needs to be done to protect our infrastructure, data, and user experiences. One of the common themes of the conference — how to secure IoT devices and the infrastructures that connect them – kept resonating throughout the day. We just need to do it. There aren’t that many surprises here — as Brian Scriber of CableLabs provocatively summed up in the final key.
- Encouraging manufacturers to implement well designed and securable code, and enabling the security capabilities and features we know to use in other technology areas.
- It is critical to protect people and devices during onboarding, the process of joining networks and configuring devices and services properly as they are first installed. We need strong device and personal identity methods, enabled through public key infrastructure solutions.
- Our communications and device operations need to ensure confidentiality and integrity while also ensuring appropriate levels of availability.
- Finally, devices must be fully supported throughout their life cycle, and this must include upgradable security and dynamic patching of vulnerabilities.
Our industry knows how to do these things — we've got over 30 years of experience securing our networks and IT systems. The lessons learned are still relevant and should be applied to the broader IoT ecosystem. But, we still see common errors like use of known insecure protocols and use of devices that don't require strong authentication, or even include default credentials so anybody knowledgeable of the device can log on. And people can find those devices through services such as Shodan — a very common theme through the day. There are opportunities for improvement such as better measurement and monitoring capabilities. Applying the benefits of data science and big data practices will help detect vulnerabilities and anomalies faster. Further, highly automated strategies to patch and reconfigure devices and networks will enable us to address threats quickly. Security's goal is to make attacking IoT sufficiently expensive so adversaries lose interest. Make it too hard or too expensive for bad actors to exploit IoT for nefarious gains.
These business, technology and policy experts provided actionable guidance, making this a unique event – and the audience and panelists left positive and confident that IoT security can be meaningfully improved if all parties share responsibility. Working collaboratively, we can ensure our customers have great experiences that enrich their lives. And we know what needs to be done. We just need to get working together to make it happen.
Join us for Innovation Bootcamp
CableLabs CEO Phil McKinney and the CableLabs team will host Innovation Boot Camp in Silicon Valley and provide a highly-focused, hands-on experience to give you the tools needed to identify, develop and pitch an innovation project.
REGISTER NOW
Security
Cybersecurity Improving the Customer Experience


Most of the time businesses view cybersecurity as a burden on their product line or enterprise operations. There is a general acceptance that security is a high-risk area that the businesses cannot ignore but is viewed by many managers and business leaders as not adding value to their bottom line; a cost akin to regulatory compliance. However, by taking this view, leaders may be losing an opportunity. Visionary executives consider cybersecurity as an area that can benefit their business through improving the customer experience.
When a cybersecurity event affects customers, usually it degrades the customer experience. This can happen in a number of ways. For example, a banking customer may not be able to access the bank's website to perform on-line banking. This was the premise for the attacks against US banks that were attributed to Izz ad-Din al-Qassam Cyber Fighters. For ISP subscribers, infected home devices send email spam, are used in Distributed Denial of Service (DDoS) attacks, steal sensitive customer information, and the customer’s data can be held hostage in ransomware attacks. Recent examples include loss of privacy from baby monitors that can be viewed and controlled by strangers outside the home and DVR that were used to take down major services on the Internet.
For cable operators, the most common types of cybersecurity attacks degrade customer video, phone or Internet services. Cable operator owned infrastructure, operator-supplied equipment, or third party purchased equipment can all be adversely impacted. For example, if a customer's computer becomes infected with malware, the customer's Internet experience from that device is degraded along with other devices on the same network. In addition, the infection drives a higher rate of calls to the cable operator's call centers, can increase the number of truck rolls to customer premises due to misdiagnosed problems, and can lead customer dissatisfaction.
This is not to say that ISPs should be primarily responsible for the cybersecurity security of their customers. ISPs have and will continue to play a role in protecting customers, but as a member of the larger Internet ecosystem. The proliferation of insecure Internet of Things (IoT) devices pollutes the Internet with malicious traffic in addition to risking theft of sensitive customer information. Addressing the problem requires the involvement of stakeholders from all across the ecosystem, not just one industry. CableLabs is helping lead the effort of improving the security of IoT devices through the Open Connectivity Foundation (OCF). We are a vocal advocate for strong device security that improves the customer experience for the device and the network ecosystem.
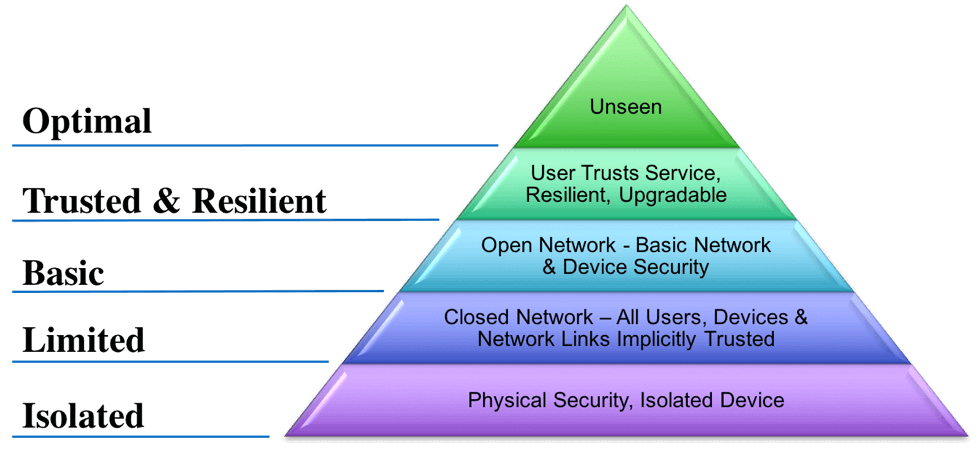
CableLabs has been working on a model to describe different levels of cybersecurity and the impact they have on customer experience. It is based on Maslow's Hierarchy of Needs and is modified from work Microsoft commissioned based on cybersecurity and reaching the full potential of the Internet. In our case, the model describes the user experience that cybersercurity plays on different types of network connected devices.
The model starts at the bottom with isolated devices. It moves up to closed networks and then to basic security on open networks. This “Basic” layer is where most home computers have operated until recently. The "Trusted and Resilient" layer is where good cybersecurity principles are considered in the product design. The device or service is resilient to attacks, upgradable and most importantly, the user has long term trust in the product. Finally, at the “Optimal” top layer, designers of products incorporate strong security controls that provide a more ideal customer experience where the security controls become less intrusive through good design but still provide high levels of protection.
Users should not have to remember passwords as the dominant authentication method. Placing secure PKI certificates in devices provides many benefits. Devices can connect automatically to authorized Wi-Fi access points and adjust to load demands. Device spoofing is dramatically reduced or eliminated. Secure end to end encryption with mutual authentication is facilitated. Software can be automatically upgraded using cryptographically validated downloads with smart defaults for end users for the design life of the product.
In connected homes, residents can centrally manage smart devices, and when the house is sold, the seller can reset the devices to remove their personally identifiable information. Software "keys" to the home can be securely transferred from the seller to the buyer without worry that the seller still has access to the devices or the home. Product designers leverage security to improve the customer experience rather than bolting it on at the end in a cumbersome manner.
Soon, consumers will have tens and hundreds of connected devices in the home and mobile networks. Unfortunately, security issues will likely get worse before they get better due to the large influx of new devices. Work needs to be done quickly to not only mitigate the damaging effects of insecure devices but to dramatically improve the security of these devices. Smart designs and architectures can leverage both good security practices and improve the user experience at the same time.
The cybersecurity system hierarchy is complex, and CableLabs is facilitating discussions with cable operators and other Internet ecosystem players in this space. Please join CableLabs on April 12-13 in NYC at our Inform[ED] Conference to continue this discussion on IoT security.