Policy
The Near Future Requires Additional Unlicensed Spectrum

Key Points
- Wi-Fi is and will remain the workhorse of consumer connectivity.
- Wi-Fi spectrum exhaust is expected to be first seen in densely populated environments due to the continued growth in connected devices and increasingly data-intensive and latency-sensitive applications.
- Additional unlicensed Wi-Fi spectrum will be critical to the continued innovation in next-generation devices and applications in education, health care and entertainment.
As we dive into a new year, new administration and new Congress, one thing remains the same: we will need more spectrum to power our increasingly data-centric lives. Almost everything we do today is online — from working, learning, accessing health care and buying groceries to streaming content. Our everyday activities rely on the exchange or consumption of data. As discussed in our prior blog, “The Case for Additional Unlicensed Spectrum,” we see that case only growing stronger every day.
Traditionally, policymakers, including the Federal Communications Commission (FCC), focused spectrum decisions around coverage, to make sure that consumers across the United States could access communications and the internet. Now that almost all of the country is covered by communications and internet services, we need to shift our priorities to focus on meeting consumers’ and the industry’s capacity and performance needs. A helpful starting point is to look at how people and businesses are consuming data now and where technology is driving more demand.
The workhorse of connectivity, Wi-Fi carries more than 90 percent of all consumer internet traffic. Looking at just mobile devices and the nation’s largest wireless providers, Open Signal found that for every one bit carried on a mobile network, nearly 9 bits are carried on Wi-Fi. Wireless providers and their networks fundamentally rely on Wi-Fi to manage their capacity and traffic because the majority of smartphone usage occurs at home, where they are predominantly connected to Wi-Fi. The overwhelming reliance on Wi-Fi is expected to continue for the foreseeable future.
The Economic Impact of Surging Wi-Fi Demand
Unsurprisingly, given the heavy consumer reliance on Wi-Fi, another recent study found that the annual U.S. economic value of Wi-Fi is expected to grow from $1.6 trillion in 2024 to $2.4 trillion by 2027, including an estimated $514 billion in consumer benefit, $624 billion in producer surplus and $1.29 billion in GDP contribution. The same study found that the FCC’s April 2020 decision to open additional unlicensed spectrum to support Wi-Fi growth (in the 6 GHz spectrum band) generated $870 billion in economic value, just from 2023-2024, and that number is expected to increase to $1.2 trillion by 2027.
The annual CES in Las Vegas always provides a preview of our increasingly connected world — from wider adoption of health care applications to richer and more immersive entertainment to new smart home applications. One primary enabler for all these applications is the ubiquitous, plentiful and inexpensive wireless connectivity provided through Wi-Fi.
Not only will these innovations add more devices and applications to the already significant load on Wi-Fi frequencies, but they will also be increasingly data intensive. The new devices and applications will increasingly require higher speeds and lower latencies to work. A recent ABI Research report projects that current-standard (6 GHz-supported) Wi-Fi devices will grow from 95 million in 2024 to 367 million in 2029 — an increase of 288 percent in just five years — in North America alone.
That’s why the Wi-Fi industry has already developed a new Wi-Fi standard that will use wider-bandwidth channels to support these types of applications and more efficiently use available unlicensed spectrum. The catch is that they need more contiguous unlicensed spectrum bands to make enough wide channels to keep pace with consumer needs and technology advances.
How We Can Evolve With Growing Demands
Without more unlicensed spectrum, Wi-Fi performance will degrade as more devices, applications and users come online. Diminished performance is expected first in areas like dense commercial and residential areas, such as universities, apartments and office buildings that host high concentrations of users and devices. As the number of devices grows and more data-intense applications become widely adopted, Wi-Fi demand will continue to grow across the country.
The expected Wi-Fi spectrum exhaustion in densely populated environments creates a problem, as roughly a third of Americans live in apartments, condos, connected townhomes or other multi-family buildings, and even more people work in office buildings with more than one tenant. Wi-Fi exhaust could start to appear within a small space, or even a block, where multiple Wi-Fi networks are operating. These networks could be supporting multiple devices per household or office and multiple users, all sharing the same unlicensed frequencies.
Initially, degraded Wi-Fi performance will occur at peak usage times. As more devices, users and more data-intensive applications — such as telemedicine and augmented reality/virtual reality (AR/VR) — start to compete for the same channels, that degraded performance will extend for more time and more broadly to more locations.
More unlicensed spectrum is the key to averting this looming problem.
Fortunately, policymakers already have a successful model to follow — the FCC’s 2020 decision to make the U.S. the first country in the world to open the 6 GHz band to unlicensed commercial use by sharing with incumbent licensees, including public safety, utility and broadcast links. Other governments around the world are following the United States’ leadership, given the significant economic and technological success.
Thanks to the U.S.’s leadership and forward-thinking, American consumers are the first to experience better, faster and more reliable Wi-Fi service almost everywhere they go. But technology will not stop advancing, and consumers will only expect better connectivity. Given the astounding growth and demand for Wi-Fi, the U.S. must again lead the way to create room for continued unlicensed innovation, establish a foothold in the Wi-Fi and unlicensed global technology markets, and model how other allied countries can create economic value, expansive access and innovation.
Below, we outline some of the technical considerations as we look more closely at the looming Wi-Fi spectrum exhaustion issue.
Unlicensed Spectrum Efficiencies Across Dimensions of Frequency, Time and Geography
Wi-Fi and other unlicensed technologies are highly efficient stewards of limited spectrum, designed to maximize the utility of every MHz of available spectrum. This enables unlicensed technologies to support a wide variety and intensity of devices, applications and use cases. Wi-Fi’s efficient use of spectrum is built on low-power use — minimizing (but not eliminating) geographic overlap of uncoordinated networks, equitable time-sharing through “listen before talk” or similar contention-management techniques, and the support for the full channelization of all available unlicensed frequencies.
- Geography: Most notably, the FCC’s 6GHz rules constrain the transmission powers of both access points and clients, limiting the coverage area of these Wi-Fi networks, therefore reducing the number of geographically overlapping networks in an area.
- Time: Wi-Fi and other similar unlicensed technologies incorporate contention-management techniques that enable geographically overlapping Wi-Fi networks to use the same (or partially overlapping) frequencies. Networks then equitably share those frequencies in time between the two or more overlapping networks.
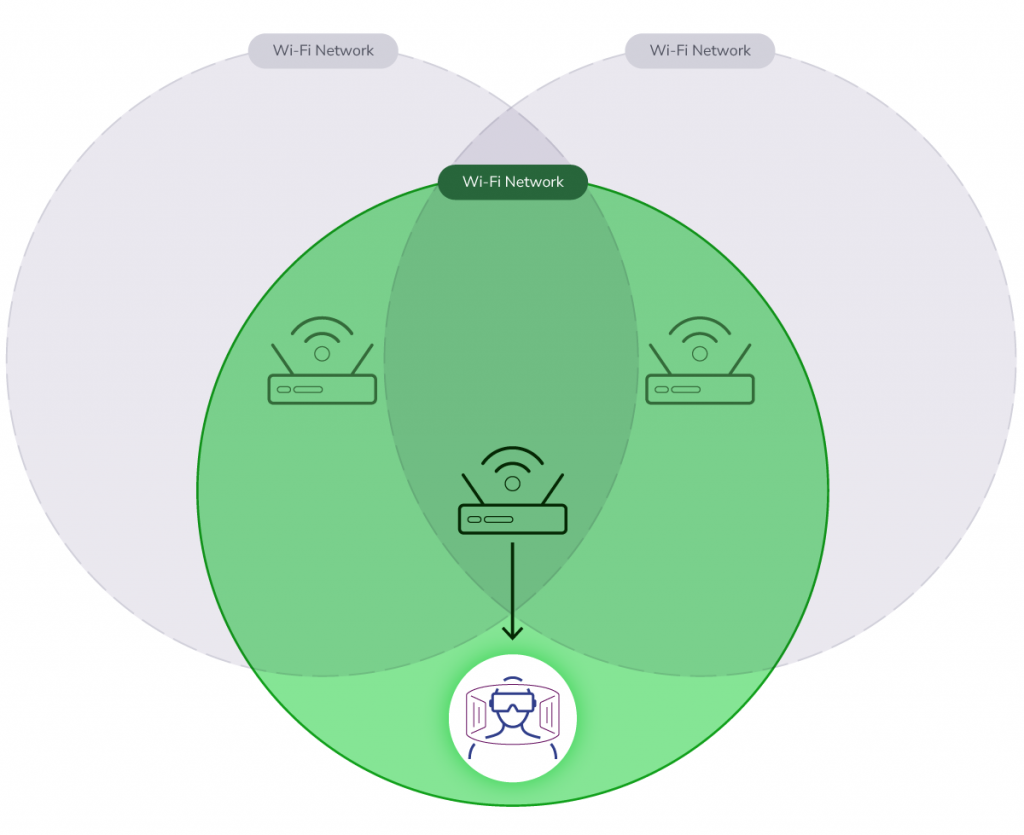
Figure 1: In general, when there are physically overlapping Wi-Fi networks on the same channel, only one network can access that channel at a time.
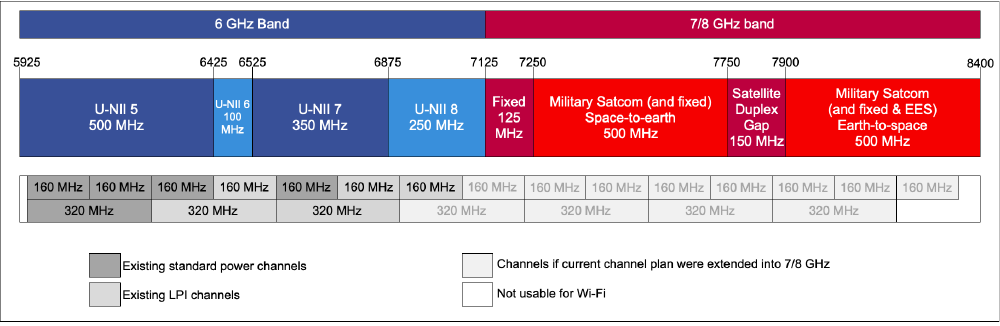
- Frequency: The 6 GHz band provides seven non-overlapping 160 MHz channels or three nonoverlapping 320 MHz channels. This has enabled geographically overlapping networks, like those in neighboring apartments, to reduce but not eliminate frequency overlap increasing available capacity to each Wi-Fi network.
Figure 2: Current Wi-Fi channelization of the 6 GHz band and potential future Wi-Fi channelization of the 7/8 GHz band. (Click image to enlarge.)
Through the dimensions of geography, time and frequency, Wi-Fi provides an incredible amount of data-carrying capacity, but it isn’t inexhaustible.
As we look to the future, these techniques, as well as further advances in Wi-Fi technology, are unlikely to meet growing demand from the devices and applications that rely on Wi-Fi — without additional unlicensed spectrum.
With additional unlicensed spectrum, however, Wi-Fi would have access to additional channels, further reducing conflict and performance degradation in networks that are close to each other and increase the instantaneous bandwidth and throughput available to applications. This would further reduce the likelihood of collisions in time.
Growing Demands Will Strain Available Unlicensed Spectrum
The explosion in the number of connected devices and the increased throughput, latency and performance demands of existing and new applications will exceed the available and future Wi-Fi capacity from currently available spectrum. As ABI Research explains, by the end of the decade, most households will have 6 GHz-capable Wi-Fi 7 access points, and we’ll begin to see the transition to Wi-Fi 8 access points.
- Total Number of Connected Devices: In 2024, the average household had 18 connected devices, but as more devices add Wi-Fi connections, such as appliances and lightbulbs, we regularly see households with 40, 50, 75 or more. ABI Research forecasts that the number of connected devices will continue to grow, with total annual shipments of Wi-Fi-connected devices to North America growing by 35.1 percent each year from 2023 through 2029. Although many of these devices are relatively low bandwidth (e.g., thermostats, lighting controls, appliances), each regularly transmits and receives data, increasing the probability of crowding and contention with other devices on the network. As the number of total connected devices increases, the amount of unused unlicensed spectrum in a home or business decreases. This will most negatively affect latency-sensitive applications, such as video conferencing and immersive, online gaming, which require ready access to uncongested spectrum.
- More Demanding Applications and Devices: The ceaseless march toward higher picture quality and the growing incorporation of AI capabilities will drive increased Wi-Fi traffic in the coming years. For instance, we see all the major streaming platforms moving toward some version of 4K Ultra HD, high dynamic range (HDR) formats (e.g., Dolby Vision and HDR10+). In parallel, smart television manufacturers are rapidly producing devices that support these more data-intensive formats. These new formats and future formats and associated devices will continue to drive and require increased bitrates. For instance, streaming a Dolby Vision video to a smart TV can easily have a bit rate of 25–30 Mbps. We expect even higher bitrates for video formats being streamed to AR/VR goggles as higher resolution and picture quality are key to these experiences. Moreover, we expect the widespread adoption of AI capabilities by device manufacturers and consumers to further drive Wi-Fi traffic, including from increased upstream video and telemetry data for AI processing in the cloud, and increased frequency and size of software updates to support locally deployed AI models.
- New Client-to-Client Connections: To further enhance the utility of 6 GHz, the FCC recently enabled very low power (VLP) unlicensed devices to use the band. With much lower power levels, VLP connections are very short range. The primary use cases for VLP include wearables, such as watches, rings and earbuds, and other short-range use cases such as connectivity between AR/VR goggles and a TV or between a gaming controller and console. What sets many of these connections apart is that the same bit will make multiple wireless hops in the home before it reaches the Wi-Fi access point and the broader internet, driving substantially more demand for unlicensed spectrum capacity.
We anticipate that the growth and increasingly intense and demanding use of Wi-Fi will first lead to unlicensed spectrum exhaust and degraded performance in the most dense environments, like apartments, condos, schools, and office buildings, before manifesting in less dense environments.
Open Additional Unlicensed Spectrum!
To enable the connection-rich near future for all end users, the U.S. government (and governments around the world) must identify additional unlicensed spectrum. Today’s growing number of Wi-Fi devices, and the next generation of devices, that support applications in education, health care and entertainment all fundamentally rely on ubiquitous, plentiful and inexpensive wireless connectivity that Wi-Fi and other unlicensed technologies provide.
Without additional unlicensed spectrum, the flow of transformative technology and applications will begin to slow down. CableLabs looks forward to continuing to work with policymakers and the broader industry to help open additional unlicensed spectrum.
Policy
The Case for Additional Unlicensed Spectrum

Key Points
- Wi-Fi provides internet connectivity for the vast majority of devices and applications, in terms of both the number of connections and total data carried.
- To keep pace with performance increases of internet services and with the growing performance demands of critical devices and applications, U.S. and global governments must continue to allocate additional unlicensed spectrum toward the advancement of Wi-Fi performance.
Today and for the foreseeable future, Wi-Fi is the technology most devices and applications use to connect to the internet. As technology advances, those devices and applications will require more data to deliver high-quality experiences for increasingly immersive, compute-intensive applications. To further support the emergence of high-fidelity video conferencing, cloud gaming, virtual reality (VR)/augmented reality (AR) and other immersive applications, widespread availability of 10 gigabit and 25 gigabit internet services is just over the horizon.
The real-time nature of these cutting-edge applications will require even faster and higher-performing Wi-Fi, with greater throughput, lower latency and better reliability. Also, because consumers primarily rely on Wi-Fi to connect to the internet — demonstrated by 10 times the amount of data going over Wi-Fi compared with mobile networks and the roughly 80 percent of data from mobile devices going over Wi-Fi — consumers now expect wall-to-wall Wi-Fi coverage in their homes, businesses and wherever they are (e.g., airports, coffee shops, civic centers). More unlicensed spectrum is key to ensuring that Wi-Fi performance keeps pace with consumer expectations and needs.
Identifying and allocating additional unlicensed spectrum for Wi-Fi is critical to ensuring the ready distribution of increasingly capable internet services throughout the home and enterprise. Such efforts will enable the increased performance of today’s and tomorrow’s critical applications in terms of coverage, throughput, latency and reliability, and will support new Wi-Fi features and functionality. In opening the 6 GHz band to Wi-Fi and other unlicensed use in 2020, the FCC took a necessary step toward enhancing the performance and capabilities of Wi-Fi and ensuring the future growth of broadband. However, opening 6 GHz isn’t a one-and-done solution. Additional unlicensed spectrum is needed to enable continued Wi-Fi performance enhancements to stay ahead of both the increasing performance of broadband networks and the growing performance requirements of devices and applications.
Background
Since its inception, Wi-Fi has been designed to use spectrum efficiently and to co-exist with other spectrum users. Wi-Fi uses a contention-based protocol and seeks to transmit data opportunistically in short bursts, when the frequency channel is available, enabling coexistence with other users. Moreover, Wi-Fi devices use a half-duplex access protocol (transmitting and receiving on the same channel) to further economize on available frequency channels.
In 1997, IEEE released the first 802.11 standard, which is the basis for Wi-Fi. From that humble beginning, we’ve seen the adoption of Wi-Fi explode. Today, there are more than 21 billion Wi-Fi devices in use globally. Initially, Wi-Fi used the 2.4 GHz band and provided a data rate of up to 2 Mbps. Over time, Wi-Fi devices began using the 5 GHz band and larger channel sizes to drive increased data rates. With Wi-Fi 6E and the incorporation of channel sizes up to 160 MHz, Wi-Fi devices can support data rates over 1 Gbps.
With the opening of the 6 GHz band (5.925–7.125 GHz), the FCC enabled for the first time 320-MHz Wi-Fi channels. Doing so required the FCC to craft an innovative three-part sharing framework to enable coexistence with the incumbent licensees:
- Low Power Indoor (LPI) requires the use of a contention-based protocol, permits only indoor access points (APs), restricts those APs to a power spectral density limit of 5 dBm/MHz and total power limit of 30 dBm EIRP on a 320-MHz channel, and is available across the entire 6 GHz band.
- Standard Power, enabled by Automated Frequency Coordination (AFC), allows outdoor access points and higher power, up to 36 dBm EIRP (or 23 dBm/MHz on 20 MHz channel), when under the control of an AFC system, and is only available in the UNII-5 (5.925–6.425 GHz) and UNII-7 (6.525–6.875 GHz) portions of the band.
- Very Low Power (VLP) requires the use of a contention-based protocol and enables indoor and outdoor operations at an even lower power limit of -5 dBm/MHz and is only available in the UNII-5 and UNII-7 portions of the band.
The Wi-Fi Alliance officially released Wi-Fi 7 on January 8, 2024. With the available 320 MHz channels in 6 GHz, Wi-Fi can now deliver speeds over 10 Gbps (using four MIMO streams), helping to ensure that Wi-Fi keeps pace with advances in internet service speeds and increasing application requirements.
Driving the Need for Additional Unlicensed Spectrum
U.S. and other governments must continue to allocate additional spectrum for unlicensed use not only to keep pace with the growing demand for Wi-Fi and other unlicensed technologies but also to remain ahead of the technology curve. Allocating additional unlicensed spectrum will fully enable and maximize the benefits of emerging applications and functionality, which will translate to an expected $5 trillion in annual global economic value by 2025. The drivers of necessary additional unlicensed spectrum are discussed below.
Increasingly capable broadband services and growing consumer demand for more connected devices, higher throughput, lower latency and increased reliability. History has made clear that total data usage and bandwidth requirements will only grow in coming years and most of that data will be carried over Wi-Fi, as noted above. This growth will be enabled by the ubiquitous availability of increasingly capable broadband services: 10 gigabit and beyond (e.g., DOCSIS 4.0, 10G-EPON, XGS-PON, 25G-PON). To this end, the U.S. government is investing well over $40 billion to deploy highly capable fiber-based networks. Data and bandwidth usage growth will also be driven by more connected devices and increased use of real-time and data-intensive applications such as new interactive VR/AR experiences. We’ve seen the average number of connected devices per home grow from 13 in 2021 to 17 in Q3 2023 — an increase of over 30 percent in less than two years and a trend we expect to continue. We also continue to see average fixed broadband residential data usage increase — currently, on average, over 640 GB per month. Moreover, the COVID-19 pandemic accelerated the adoption and use of video conferencing and other cloud-based tools. As the FCC has explained, “video conferencing has grown from a niche product to a central pillar of our communications infrastructure.” Because consumers no longer connect devices using an ethernet cable, but rather rely on Wi-Fi to connect to the internet, the government must also continue to make additional unlicensed spectrum available to ensure the government’s investment in broadband deployment actually reaches end-devices and enables the critical applications of today and tomorrow.
Supporting new features and functionality of Wi-Fi 7 and beyond. Additional unlicensed spectrum is also needed to make room for the coming features and functionality of Wi-Fi 7 and beyond. The release of Wi-Fi 7 introduced new features and functionality; of note, Wi-Fi 7 now includes support for 320 MHz channels and Multi-Link Operation (MLO). Both features enable higher throughput and lower latency through the use of wider channels and multiple channels — features not available in prior generations of Wi-Fi. Moreover, IEEE is already working on 802.11bn, the standard that will underpin Wi-Fi 8. The emerging focus is on Ultra High Reliability (UHR) where additional spectrum becomes even more critical to meet performance goals in light of potential channel contention from high-density client environments, adjacent Wi-Fi networks or other unlicensed use.
The technical limitations enabling the 6 GHz innovative sharing framework. The FCC’s innovative unlicensed sharing framework in 6 GHz is a huge success, protecting mission-critical incumbents and allowing for expanded Wi-Fi use at the same time. Moreover, this sharing framework eliminated the need to relocate incumbents, enabling the rapid realization of the benefits of this additional unlicensed spectrum to consumers and enterprise users alike.
To ensure safe coexistence, the FCC established a detailed unlicensed spectrum sharing framework, including Low Power Indoor-only (LPI) restrictions across the band and more recently Very Low Power (VLP) restrictions and database-controlled (by an AFC database) standard-power capabilities available in certain parts of the band, as detailed above. To accommodate these restrictions, Wi-Fi requires more bandwidth to deliver high speeds and employs more spectrum-intensive techniques, such as mesh networking, to achieve the needed coverage. For example, mesh networking requires additional overhead to backhaul and coordinate the mesh traffic, reducing the overall data-carrying capacity of the available channels. One approach to avoid mesh networking is to use a higher-power channel. However, under the current FCC rules, Wi-Fi can access, at most, only one standard-power 320 MHz wide channel through an AFC system.
Between the power limits and other regulatory restrictions placed on LPI and VLP operations and the limited availability of standard power channels under an AFC, the 1,200 MHz available for unlicensed use in the 6 GHz band is unable to provide the needed coverage, throughput, capacity and latency performance that will be expected and required by consumers and enterprise users in the near future. Additional unlicensed spectrum will allow consumers and enterprise users to more fully benefit from Wi-Fi 7’s new features, enabling better user experiences.
It’s Up to Government
Taking all these drivers into account and considering the value that unlicensed spectrum will continue to deliver to global economies, the United States and other governments around the world should waste no time identifying meaningful additional unlicensed spectrum, particularly given that any additional unlicensed spectrum will likely have similar regulatory technical limits as 6 GHz unlicensed use.

Security
Raising the Bar on Gateway Device Security

Today, CableLabs® has publicly released a set of best common practices (BCP) to enhance the security of cable modems, integrated access points, and home routers (collectively, known as “gateway devices”) against malicious activity and other cyber threats. This work builds on and extends CableLabs’ and the cable industry’s longstanding leadership in cybersecurity to ensure a consistent and robust baseline for gateway device security, increased economies of scale, and an ontology for simplified communication and procurement between network operators and device manufacturers.
The BCP Working Group is comprised of security technologists from CableLabs, network operators from around the world, and gateway device manufactures, including representatives from CableOne, Charter, Cisco, Cogeco, Comcast, Commscope, Cox, Liberty Global, MaxLinear, MediaCom, Shaw and Technicolor. In developing the BCP, the Working Group drew heavily upon well-established and widely accepted security controls, recognized broadly by industry and government security experts.
The cable industry has long employed extensive network security practices to ensure the confidentiality, integrity and availability of broadband services, including gateway devices. The BCP expands and standardizes these network security practices for gateway devices and complements cable operators’ broader set of security practices. For instance, DOCSIS® Security testing is performed on all gateway devices to ensure DOCSIS protocol conformance, including the verification of the correct implementation of public key infrastructure (PKI) authentication and identity management, BPI+ encryption, and EAE (Early Authentication and Encryption) secure provisioning requirements.
The BCP document goes beyond DOCSIS Security requirements and provides a framework for the full range of security considerations applicable to gateway devices, including hardware and manufacturing considerations, default security settings, configuration procedures, secure boot, roots of trust, software/firmware development and verification, encryption requirements for both data in transit and data at rest, and physical security, among others. To further ensure the robustness of the BCP, the working group compared and mapped the BCP to NIST’s general guidance for connected devices used by the federal government, to help confirm the scope was fully comprehensive of applicable security considerations.
The BCP represents the industry coalescing around a common set of security baseline requirements that furthers the following critical goals:
- Provide a common framework for security elements and controls within gateway devices, including cable modems, integrated Wi-Fi access points, and home routers, to align the varied approaches to device security across the industry.
- Create a community of manufacturers and network operators collaborating to enhance gateway device security.
- Leverage well-established and well-vetted security controls and practices to minimize the risk of unknowingly introduced vulnerabilities or other security weaknesses.
- Harmonize security requirements across network operators to drive increased economies of scale, lowering the cost of broadband deployment.
- Further protect network resources and broadband service from malicious attacks.
- Provide a framework for network operator assurance that enables verification of testable practices and configurations.
- Enable alignment across standards, regulatory, and compliance regimes through a transparent and open set of best common practices.
- Establish a security framework for gateway devices that builds in flexibility and agility, so that manufacturers and network operators can address and adapt to new threats and changes in the cyber risk landscape.
While this initial release is an important achievement, one that strives to be comprehensive in terms of security posture for gateway devices, we all recognize that this field is constantly evolving and advancing. We see the BCP as a framework that must and will be updated and maintained as network technology, device security, and unfortunately, adversary techniques continue to evolve. To that end, we invite and welcome additional gateway and modem manufacturers as well as additional network operators to join the working group as we continue to progress this effort.
On October 13, 2021, at 3:00 pm ET, we invite you to join our virtual panel session at SCTE Cable-Tec Expo to discuss and further explore Gateway Device Security and our work to develop the BCP.

HFC Network
How Reliable Is Cable Internet? Here’s How Our Networks Are Performing

Starting in mid-March, the world experienced a sudden surge in internet usage driven by the widespread COVID-19 stay-at-home orders that caused many of us to switch to working and studying at home in a matter of days. Cable broadband networks not only withstood this sudden surge in internet usage; they excelled. For example, for the week of June 27–July 4, 99.9 percent of U.S. cable broadband users saw no material impact on customer experience. Looking to the future, cable networks are also well-positioned to remain ahead of sustained increases in consumer demand. Although internet usage appears to have plateaued recently, CableLabs and the broader cable industry continue to develop further network advancements to ensure that internet performance stays well ahead of even the most demanding home users’ needs for years to come.
Internet Usage During COVID-19 and Cable Broadband Services
Network monitoring provider OpenVault reveals just how much home internet usage jumped over the past few months:
- In the United States, average daily downstream consumption from 9 a.m. to 5 p.m. in the first week of April totaled about 6.35 GB per household, up 42 percent from 4.46 GB in January. Upstream average usage during business hours rose to 0.39 GB, up 83 percent compared with 0.22 GB in January.
- Worldwide, looking at a sample of 500 fixed, mobile and Wi-Fi network providers, networking equipment provider Sandvine found that overall traffic increased 40 percent between February 1 and April 19. It also found that upstream traffic rose 121 percent during this period.
Even considering these dramatic increases, home internet use remains heavily asymmetrical. The amount of data transmitted to the home (downstream) vastly outweighs the amount of data transmitted from the home (upstream). This is driven by the continued use of video streaming services (e.g., Netflix, YouTube) that require substantial amounts of data to be transmitted to the home to enable the user to view a movie, TV show or other video. These applications require very little data transmitted from the home.
Two-way video collaboration tools (e.g., Zoom, Microsoft Teams) do require more data to be transmitted from the home (upstream) in comparison with video streaming services due to two-way audio and video functionality. Even with the increased use of these collaboration tools, upstream data transmissions remain well below a tenth of total data transmitted over home internet connections.
The predominance of downstream use is further confirmed in the detailed examination of broadband use from a top-tier North American cable broadband operator, as set forth in Figures 1 and 2 below. Over the past 8 years, the proportion of downstream traffic has increased and plateaued at roughly 92–94 percent of total traffic at peak. Looking more closely at the most recent 5 months illustrates the rapid increase in internet use due to COVID-19. Even with upstream increasing at a faster rate than downstream, upstream use at peak maxed out at only 9 percent of total traffic, as illustrated in Figure 2. Additional metrics, trends and observations on cable internet usage can be found on NCTA’s COVID-19 Dashboard.
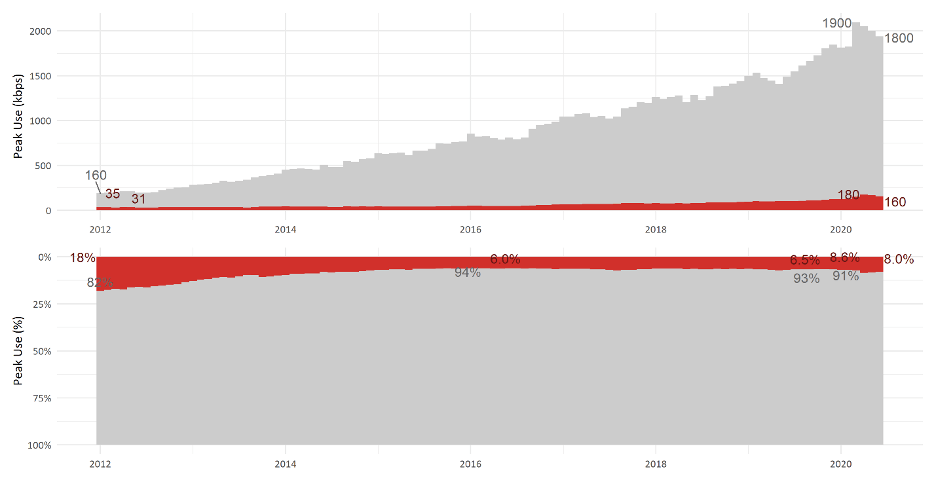
Figure 1: 2012 through June 2020, Average Downstream and Upstream Peak Use (kbps and %) per Subscriber from a Top-Tier North American Cable Broadband Operator
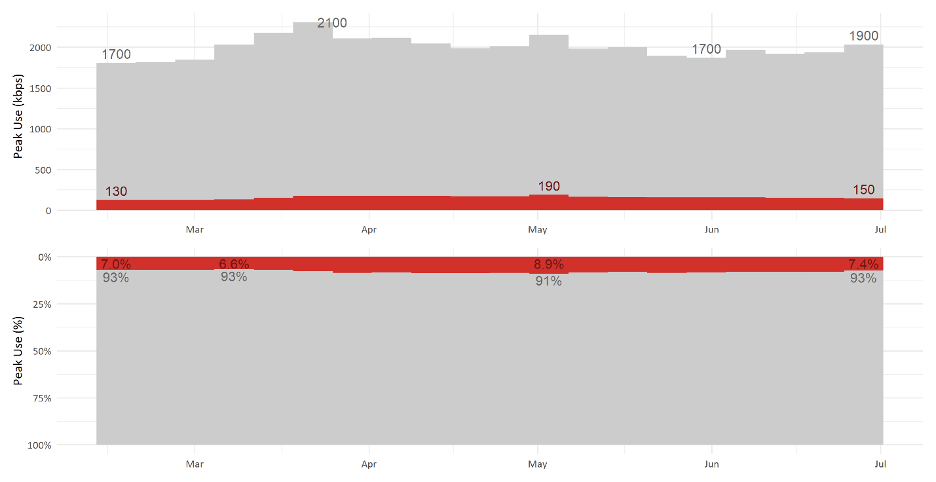
Figure 2: Mid-February 2020 through June 2020, Average Downstream and Upstream Peak Use (kbps and %) per Subscriber from a Top-Tier North American Cable Broadband Operator
Cable Broadband’s Outlook Is Healthy
The asymmetric design of cable’s internet service tiers accurately matches how consumers have been using the internet, even with the increased use during stay-at-home orders. This is important both to ensure a high-quality user experience and to efficiently allocate available network capacity. Cable operators continually monitor their networks and engineer them to accommodate significant fluctuations. There are indications that these increased levels of usage will be foundational as new use cases emerge and as a significant segment of the population continues to work and learn from home. For example, many companies have found that their remote workers maintained or even improved productivity—so much so that they may make the arrangement permanent.
Cable network technology, more formally known as Data Over Cable Service Interface Specification (DOCSIS®), has the flexibility and performance capabilities to handle further increases in consumer demand in both downstream and upstream data transmissions. With DOCSIS 3.1 technology, the current widely deployed version of cable network technology, cable operators are making gigabit services broadly available. For example, cable gigabit services are now available to 80 percent of U.S. housing units.
And there are more performance enhancements on the horizon with the recently released DOCSIS 4.0 specification, which will readily enable multi-gigabit internet services. In addition, the 10G platform provides increased reliability, enhanced security and reduced latency.
Taking a peek into the future, cable broadband networks have not only excelled in the initial surge in internet usage caused by the COVID-19 pandemic, but they will be ready for the potential long-term changes in consumer behavior that will drive increased internet usage. To learn more about the technologies that power cable’s broadband internet services today and into the future, click the button below.

Policy
Driving Increased Security in All IoT Devices

CableLabs engages with the IoT industry and the broader stakeholder community, including governments, to help drive increased IoT device security. The rapid proliferation of IoT devices has the potential to transform and enrich our lives and to drive significant productivity gains in the broader economy. However, the lack of sufficient security in a meaningful number of these newly connected devices creates significant risk to consumers and to the basic functionality of the Internet. Insecure IoT devices often serve as building blocks for botnets and other distributed threats that in turn perform DDoS attacks, steal personal and sensitive data, send spam, propagate ransomware, and more generally, provide the attacker access to the compromised devices and their connections.
To help address the challenge of insecure IoT, CableLabs along with 19 other industry organizations came together to develop “The C2 Consensus on IoT Device Security Baseline Capabilities” released earlier this week. The broad industry consensus identifies cybersecurity baseline capabilities that all new IoT devices should have, as well additional capabilities that should be phased in over time. The development kicked off in March with a workshop hosted by the Consumer Technology Association (CTA). Over the past months, the group has coalesced around the identified cybersecurity capabilities. These include capabilities in the areas of device identity, secured access, data protection and patchability, among others.
CableLabs has also engaged with the National Institute of Standards and Technology (NIST) as it develops its recently released draft report, “Core Cybersecurity Feature Baseline for Securable IoT Devices: A Starting Point for IoT Device Manufacturers.” Both industry and governments largely agree on the capabilities that must be included to increase device security. Like the C2 Consensus, NIST focuses on foundational cybersecurity capabilities, including device identity, secure access, patchability of firmware and software, protection of device configuration and device data, and cybersecurity event logging.
The cybersecurity capabilities identified in the C2 Consensus and NIST will help prevent and minimize the potential for exploitation of IoT devices. Both documents provide a strong foundation and help point IoT manufacturers in the right direction on how to increase device security. However, cybersecurity is an ongoing journey, not a destination. Security practices must evolve and continue to improve to address new and emerging threats and changes in technology. This foundation must continue to be built on overtime.
CableLabs has long been a leader in the development of security technologies. For decades, CableLabs has helped guide the cable industry in incorporating many of the identified security capabilities into cable devices and has ensured the maintenance and advancement of these capabilities over time. For instance, since the first DOCSIS specification in 1997, CableLabs has helped ensure the protection of data: All traffic flows between each cable modem and the CMTS are encrypted to protect the confidentiality and integrity of those transmissions. This is not a once-and-done process; CableLabs has and must continue to advance the cryptography used in cable devices to protect against new and more powerful brute force attacks and other potential threats. Similarly, nearly 20 years ago, CableLabs adopted PKI-based digital certificates to support strong device identity and authentication for devices connecting directly to the cable network (e.g., cable modems, Internet gateways, set-top boxes). Since the initial implementation, CableLabs has continued to advance its PKI implementation to address new and emerging threats.
CableLabs has leveraged its experience and success in developing and implementing cybersecurity technologies in cable devices to help drive increased security in IoT devices. The underlying fundamentals, as well as many of the approaches to implementing, are transferable to IoT, as detailed in our white paper, “A Vision for Secure IoT”. We’ve not only engaged with the C2 Consensus and NIST’s IoT security efforts, but also in industry specification organizations, specifically the Open Connectivity Foundation (OCF)—to develop secure interoperability for IoT devices. OCF has implemented nearly all of the identified capabilities in its specification, tests for the capabilities in its certification regime, and provides the capabilities, free of charge, in its open source reference implementation – IoTivity.
Since publishing “A Vision for Secure IoT” in the summer of 2017, industry and the broader stakeholder community, including governments, recognize and have begun to address the challenge of insecure IoT.

Events
CableLabs Sponsors FCBA/IAPP “Data Is King”

Many of today’s most popular consumer products and services are powered by the exponential growth in the generation, collection and use of personal data, enabled by ever-increasing broadband capacity, processing power and storage. These products and services provide consumers with unparalleled personalization, efficiency and convenience. However, the technologies and practices surrounding personal data also create new dimensions of risk to individuals, institutions and society alike.
In response, governments both in the United States and around the world are under increasing pressure to develop new legislation and regulatory models to address these growing concerns. In the past year alone, we have seen the implementation of the European Union’s sweeping General Data Protection Regulation (GDPR), the passing of the California Consumer Privacy Act, and multiple hearings in the U.S. Congress stemming from numerous data breaches and other scandals involving the potential misuse of consumers’ personal data. Here at CableLabs, we recognize the interplay and potential impact of emerging privacy regulations on the direction of next-generation Internet applications.
In that spirit, CableLabs sponsored “Data Is King” – U.S. Privacy Developments and Implications for Global Markets and Technology Development, a recent event co-hosted by the Federal Communications Bar Association (FCBA) Rocky Mountain Chapter and the IAPP Denver/Boulder KnowledgeNet Chapter. The event gathered luminaries from across the policy and technology spectrum to explore trends and recent developments in privacy law and regulation, as well as the potential impact that these policies will have on the products and services of tomorrow.
The event was kicked off by Martin Katz (Chief Innovation Officer and Senior Advisor for Academic Innovation and Design at the University of Denver and the Executive Director at Project X-ITE). Katz discussed the existing gaps and fragmentation in today’s U.S. privacy regime and highlighted the drawbacks of the EU’s approach to comprehensive personal data protection legislation (GDPR). In Katz’s view, such an approach creates a significant and costly compliance regime that can stifle new startups and small businesses, and more generally, innovative new products and services. He emphasized that any comprehensive U.S. federal regime should recognize and seek to minimize compliance costs and ensure room for innovation while protecting consumer choice, trust and accountability.
Tracy L. Lechner (Attorney and Founder at the Law Offices of Tracy L. Lechner) moderated the first panel session, focused on trends and recent developments in privacy regulations domestically and internationally, with the following panelists: Beth Magnuson (Senior Legal Editor of Privacy and Data Security at Thomson Reuters Practical Law); Dale Skivington (Compliance and Privacy Consultant, Adjunct Professor at the University of Colorado, and Former Chief Privacy Officer at Dell); Erik Jones (Partner at Wilkinson, Barker, Knauer); and Scott Cunningham (Owner at Cunningham Tech Consulting and Founder of IAB Tech Lab).
The panelists agreed that the general position of industry has evolved from a preference for best practices with agency oversight to a recognized need for U.S. federal legislation. This shift has been spurred by a desire for a common compliance framework in light of developing differences in state laws and diverging international privacy regimes. The panelists emphasized that changing privacy regulatory requirements has forced organizations to make frequent and costly IT overhauls to ensure compliance that arguably create little to no value for consumers. For instance, GDPR’s expansive definition of “personal data” created a herculean project for large organizations to take the foundational step of identifying and classifying all the potentially covered data. The panelists agreed that state attorneys general could have a valuable and thoughtful role in enforcement, but they also believe that specific requirements should be standardized at the federal level and be based on an outcome- or risk-based approach, unlike GDPR’s highly prescriptive approach.
Mark Walker (Director of Technology Policy at CableLabs) led a second-panel discussion, focused on the interplay of privacy regulation and technology development. The panel featured Walter Knapp (CEO at Sovrn), Scott Cunningham and Danny Yuxing Huang (Postdoctoral Research Fellow at the Center for Information Technology Policy at Princeton University). Walker framed the panel discussion in historic terms, highlighting the privacy concerns generated through the widespread availability of the portable camera in the late 1800s, through the emergence of electronic eavesdropping capabilities in the 1960s and, more recently, through the broad adoption of RFID technology. For each of these examples, public concern drove legal and regulatory changes, but more fundamentally, the privacy “panic” subsided for each technology as society became more familiar and comfortable with each technology’s balance of benefits and drawbacks.

Through that lens, the panelists examined GDPR and highlighted the high associated compliance costs, from both a technical implementation and revenue perspective. Faced with these costs, many smaller publishers are choosing to cut off access to their content from covered geographies rather than trying to comply. In comparison, large Internet firms have the resources to ensure compliance even in a costly and highly fragmented regulatory environment. Until recently, the Internet has largely matured without defined geographic borders and has nearly eliminated global distribution costs for smaller publishers. However, this trend may be reversed in the face of an emerging fragmented and highly regulated environment, reducing the viability of smaller publishers and driving unintended market concentration.
Turning to emerging technologies, Huang described his research into the security and privacy implications of consumer Internet of Things (IoT). He provided an overview of a newly released research tool, Princeton IoT Inspector, that consumers can easily use to gain detailed insights into the network behaviors of their smart home IoT devices. Through this tool, consumers can gain a better understanding of how IoT devices share their personal information. He illustrated how IoT Inspector was able to identify the numerous ad networks and other domains a streaming video device communicated with while streaming a single television program; surprisingly, the streaming device communicated with more than 15 separate domains during that single streaming program.
The event closed with Phil Weiser, Colorado’s Attorney General, providing keynote remarks that outlined the current state of legislative efforts, explained potential approaches that address key privacy challenges and highlighted the role of state attorneys general in developing regulatory approaches and enforcing them. Attorney General Weiser recognized that although curbing a patchwork of state laws in favor of a single federal one would be the ideal outcome, it is unlikely to happen in a reasonable timeframe, saying:
A first best solution would be a comprehensive federal law that protected consumer privacy. Such a law, like the Dodd-Frank law, should authorize State AGs to protect consumers. When Congress starts working on such a law, I will be eager and willing to support such an effort. After all, differing laws and reporting requirements designed to protect privacy creates a range of challenges for companies and those working to comply with different—and not necessarily consistent—laws.
In today’s second-best world, I believe that States have an obligation to move forward. We should do so with a recognition that we need to collaborate with one another and develop approaches that recognize the challenges around compliance. We can use your help and engagement and we work towards just this end.

As CableLabs continues to focus on developing new and innovative network technologies, we must continue to ensure that we have a sound understanding of the rapidly evolving privacy landscape, both here and abroad. But, just as importantly, policymakers should have a sound understanding of how the various regulatory approaches may impact current and developing technologies. Events like this help bridge those gaps in understanding.

Policy
Driving Global Connectivity Well Beyond Cable Technology

CableLabs participates in more than 30 unique standards organizations, industry consortia, and open source efforts.
CableLabs is focused on developing innovative technologies, not only in the performance of cable’s hybrid fiber coax (HFC) networks, but also in many areas that extend beyond the traditional cable network, including wireless (both licensed and unlicensed), cybersecurity, network function virtualization (NFV), optical technologies for access networks, and the application of artificial intelligence (AI) and machine learning to network management and orchestration. To be successful, CableLabs recognizes that, in these areas beyond traditional cable technology, it must engage and work with the broader technology community to drive advancements. This effort is visible through CableLabs’ deep commitment to leading and contributing to standards organizations, industry consortia, and open source efforts in these broader areas.
Developing standards and industry specifications are at the core of CableLabs, which has been in the specification and standardization business since its inception over 30 years ago. In 1997, CableLabs released the initial version of the Data Over Cable Service Interface Specification (DOCSIS), the technology that enables broadband service to be provided over an HFC network. Standardization of the cable interface specification allowed the cable network operators to work at scale with the network equipment manufacturers to build the interoperable technology needed for cable to meet the exploding demand for broadband Internet access.
Ever since, CableLabs, along with its members and the vendor community, has continued to advance DOCSIS technology. Cable operators today have largely moved to DOCSIS 3.1 technology, enabling the availability of gigabit-speed broadband across nearly the entire cable footprint in the US, and driving towards a “10G” network capability. As cable has broadened its focus, CableLabs has responded by broadening its standards efforts and industry engagement.
Improving Wi-Fi and Enabling 5G through Wireless Standards Engagement
CableLabs contributes significantly to almost a dozen different standards organizations to improve wireless connectivity through standardization related mechanisms. Our work is not restricted to improvements in the traditionally separate spheres of in-home and mobile wireless and includes work toward a seamless network convergence for the future. Along those lines, CableLabs is engaged in the O-RAN Alliance, where we are leading an effort to establish an open virtualized RAN (“radio access network”) fronthaul specification which will allow for low-cost small cells with DOCSIS network backhaul.
At 3GPP, CableLabs is driving the Wireless-Wireline Convergence (WWC) effort to make the operation, management, and traversal of 5G wireless networks and 10G DOCSIS networks more seamless. CableLabs is also working to bring consumers a faster and safer in-home network experience through a next-generation adaptive security platform, CableLabs ® Micronets, which enables enterprise-level smart security at home. Beyond making home networks safer, we’re working to make them more powerful; exhibited by our role in achieving recent milestones with carrier-grade Wi-Fi certification through the Wi-Fi Alliance’s VantageTM and launch of the new EasyMeshTM certification program.
Driving Increased Performance of Optical Technologies in the Access Network through Broad Industry Collaboration
As cable drives its fiber infrastructure deeper into the HFC network, CableLabs has developed new technology for use of fiber in the access portion of the network and has promoted standardization of such technology. We are involved at several global standards development bodies—including IEEE, ESTI, O-RAN, and SCTE where we work to level-up all aspects of the fiber network. These efforts combine our internal specification development— work (such as Coherent Optics specifications) with broad industry collaboration in order to deliver dramatic improvements to the access network across all areas. This means that while working toward ever faster speeds through developing the next generations of PON protocols, the whole network ecosystem needs to be addressed, which includes innovation in network operations with projects such as Proactive Network Maintenance (PNM).
Building a Common, Secure, Foundation for IoT Devices of the Future
CableLabs envisions a future empowered by technologies that improve our lives—a future where augmented reality (AR)/ virtual reality (VR) head-mounted displays, video walls, AI-enabled media, ubiquitous Internet of Things (IoT) devices, light field holodecks and displays (as seen in our latest Near Future video) are just the beginning. However, in order for AR/VR devices to be populated with high-quality content, for video walls to connect seamlessly, or for our IoT devices to assist us securely, we will first need high-quality, secure, industry-driven standards on which the technology and applications can be built. This belief has led to our involvement in the Open Connectivity Foundation (OCF), an industry effort to develop a secure interoperability specification for IoT.
Catalyzing the Future of Immersive Media Experiences
Recognizing the importance of building consensus throughout the ecosystem, even beyond the broadband network, CableLabs is significantly involved in and contributing technical expertise toward a number of emerging technology areas, including significant projects in video, VR/AR, and immersive media. Essential to the actual adoption of standards, we recently played a founding role in establishing Media Coding Industry Forum (MC-IF) to address patent licensing of future MPEG codecs. In addition, we announced a new collaboration called IDEA (Immersive Digital Experiences Alliance) to establish and promote end-to-end delivery of immersive content, including light fields, over broadband networks.
To learn more about our work in standards, open source, and industry consortia please see our members-only (login required) Standards Strategy Update (April 2019) on current engagements.

Policy
The Gigabit Internet Dream Continues to Expand

Cable gigabit service availability continues to expand – as of June 2018, 63% of U.S. housing units – 74% of the cable broadband footprint – had gigabit service or better available from their local cable operator. This is up seven percentage points in just three months and has expanded by 16X in 18 months. Cable is making the gigabit Internet dream a reality. Coincident with this update of the cable industry’s gigabit deployment data, we are also releasing a new installment in our Inform[ED] Insights series that explains the technology that enables these gigabit networks.
Cable’s deployment of high-capacity broadband networks is enabling the gigabit services of today and the symmetric multi-gigabit services of tomorrow. With the wide availability of gigabit service and beyond, the broadband infrastructure is in place to power emerging technologies that will transform and enhance our lives through immersive entertainment, next-generation healthcare and a reimagination of education and work.
CableLabs and the cable industry are continuing to advance the capacity and performance in each segment of the cable broadband network to remain well-ahead of consumer demand. We are focused on developing innovative network technologies in the areas of coax (e.g., DOCSIS 3.1 and full duplex DOCSIS), fiber (e.g., coherent optics in the access network), and wireless (e.g., Wi-Fi and 5G), as well as defining optimal network architectures to provide the necessary capacity and performance in each segment of the network for today’s gigabit services and those anticipated in the future.
Ready to see how the cable industry is driving gigabit speeds from the lab to the consumer? Click on the link below to download our new Inform[ED] Insights white paper.
Innovation
Living the Gigabit Internet Dream
“Gigabit” is the Internet dream. It means connectivity at blazing-fast speeds, with enough bandwidth for any device imaginable, where the online world is your oyster. Cable is rapidly making this dream a reality by making gigabit Internet service available to consumers.
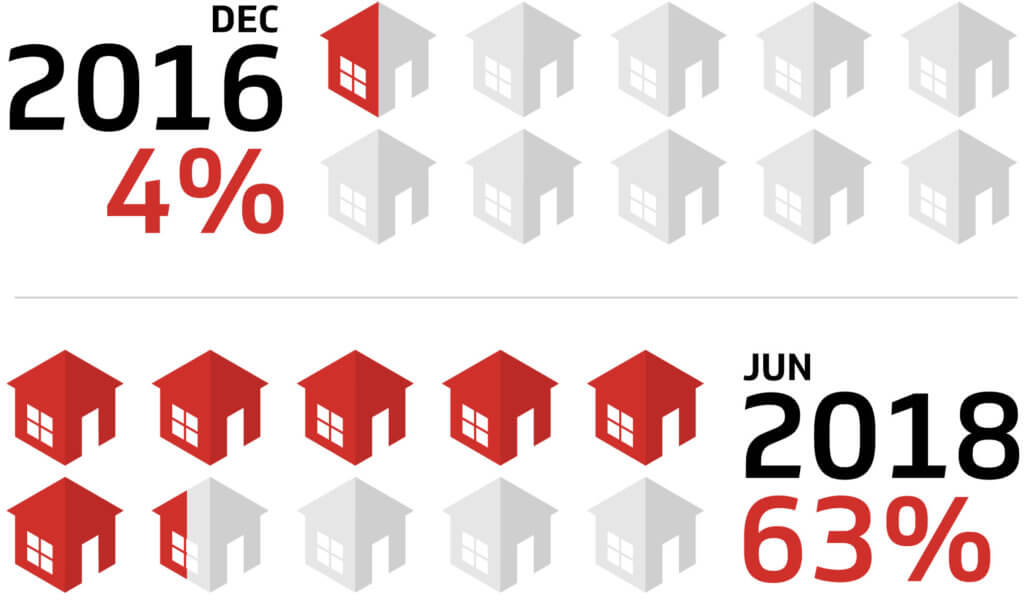
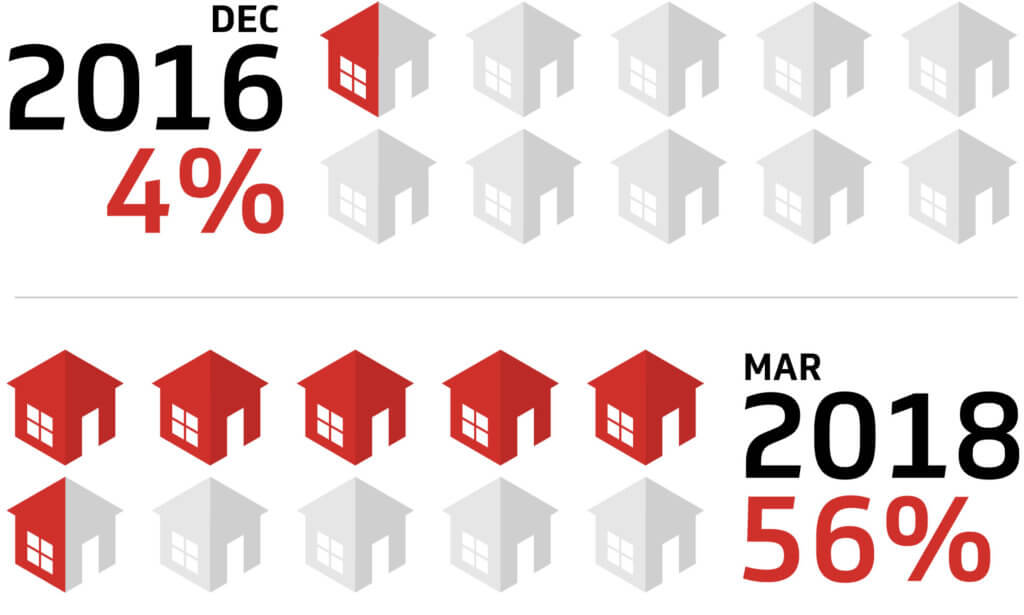
Looking back just a couple of years, the prospect of widely available gigabit service was unimaginable. As of December 2016, only 4% of US housing units had cable gigabit available. In just fifteen months, cable operators in the US have increased that number by 14X. CableLabs regularly surveys our members, and we know that as of March 2018, 56% of US housing units – 66% of the cable broadband footprint – had gigabit service or better available from their local cable operator. That number is poised to climb higher as DOCSIS 3.1 technology is deployed across cable networks.
But, This is Only the Beginning of the Story
CableLabs and the cable industry are investing in further network innovations to enable broadband technology to stay well ahead of customer demand for years to come.
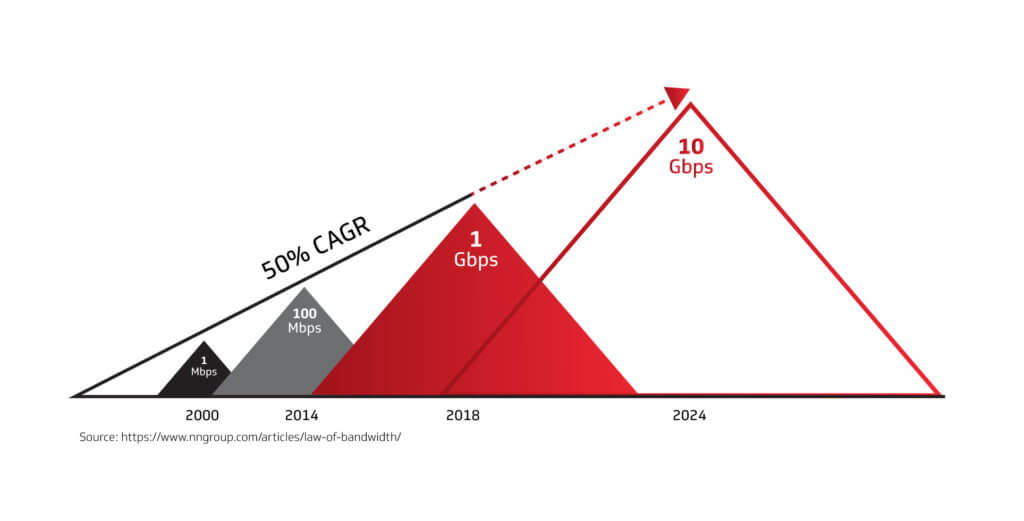
Over the past 35 years, available consumer Internet speeds have followed what is known as Nielsen’s Law, increasing at roughly a 50% compound annual growth rate. Gigabit service is just the latest step in the history of ever-increasing speeds. If past is prologue, we can expect to see the availability of 10-gigabit service offerings around 2024, enabling experiences that are difficult to imagine today.
Pushing the Gigabit Internet Envelope
The cable industry is preparing for our ever-faster future. We’re examining each segment of the network and developing new technologies to advance the performance of cable networks. The main elements of our work to drive further capacity and performance are:
- DOCSIS: CableLabs is currently working to commercialize the next generation of DOCSIS technology. Full Duplex DOCSIS 3.1 will enable cable operators to provide symmetric gigabit service to customers – eliminating the upstream constraint and fully unleashing the power of cable.
- Fiber: To ensure sufficient capacity in the fiber portion of the cable network, CableLabs has focused on adapting coherent optics. Coherent optic technologies have the potential to increase the per-strand capacity in cable networks by orders of magnitude over currently available digital optics technologies. This is an essential element in cable’s fiber-rich networks to deliver greater performance for consumers.
- Wireless: We all experience our broadband service through our Wi-Fi connection. So, our ability to take full advantage of cable network advancements depends on the performance of that Wi-Fi connection. To ensure the reliability and improve the overall performance of Wi-Fi, CableLabs has developed protocols for Wi-Fi proactive network maintenance (Wi-Fi PNM) to quickly solve connectivity problems, advanced global standards for Wi-Fi to usher in next-generation technologies, and increased wireless bandwidth through spectrum policy engagement.
The continued innovations of CableLabs and the cable industry have enabled cable operators to provide broadband service that is well ahead of consumer demand. Cable networks are high-capacity, efficient, and future-ready to meet ever-increasing consumer demand for broadband performance.
For more information on how the cable industry is driving gigabit speeds from the lab to the consumer, please click below.

Events
CableLabs Hosts “Cyber Risks in an IoT World”

Security provides the fundamental trust that enables the growth of broadband, and as the number of connected devices grows rapidly, all actors must make it a priority. The cable industry’s security expertise and investment positions it to play a constructive role in this rapidly evolving, global challenge. Here at CableLabs, we continue to focus on cybersecurity in our innovation and R&D work, and we recognize the interdependence of public policy and technology developments in this area.
In that spirit, we recently hosted an event at our facilities in Colorado entitled Cyber Risks in an IoT World, which was co-presented by the Rocky Mountain Chapter of the Federal Communications Bar Association (FCBA) and Silicon Flatirons. Our primary goal was to shine a spotlight on key elements of federal cybersecurity policy and the evolving risk faced by enterprises in light of the rapid proliferation of Internet of Things (IoT) devices. The event featured Evelyn Remaley, Deputy Associate Administrator at the Office of Policy Analysis and Development of the National Telecommunications and Information Administration, U.S. Department of Commerce, among other notable speakers and attracted over 60 attendees from the local and regional technology policy and legal communities.
CableLabs’ Rob Alderfer kicked off the event by laying out the broader context, including the trends that are driving increased risk to consumers and the basic functionality of the Internet. With the constant barrage of new cyber incidents, often driven by IoT devices vulnerable to exploitation, governments at all levels are taking notice and grappling with the rapidly evolving threat. Cybersecurity is no longer the domain of the IT department, but rather a key area of governance for all enterprises. You can read more about our vision for improving IoT cybersecurity here.
Clete Johnson (Wilkinson Barker Knauer, LLP) provided a primer on federal cybersecurity policy that cast the Internet and enterprise networks as the battlefields, espionage platforms, and crime scenes of the 21st century. The current regulatory landscape can be subdivided into several broad areas: the threat environment, the policy environment, government activities, and the developing policy consensus across government and industry. The threat environment is characterized by the increasing number of more and more severe attacks. These attacks originate from both non-state actors (organized crime groups, proxies for nation-states, hacktivists, and, potentially, terrorists) as well as state actors (Tier I intelligence services and their allies and partners). However, the line between non-state and state actors often blurs and these groups often overlap. Johnson also detailed the developing policy consensus that centers around dynamic, flexible risk management; a shared responsibility across all stakeholders; mutually beneficial public-private partnerships; and a move beyond the “punish the victim” enforcement. This developing consensus is largely embodied in the Cybersecurity Executive Order and its implementation.
Evelyn Remaley (NTIA) delivered the keynote presentation on the Cybersecurity Executive Order, the developing Botnet Report required by the Order, and, more broadly, the NTIA’s work in cybersecurity through the multi-stakeholder process. Remaley emphasized that NTIA recognizes the complexity of the ecosystem and sees it as a multi-textured and evolving global system that requires an agile, inclusive cyber policy approach. Two truths underlay that perspective:
- To protect innovation, there must be stakeholder-driven policy outcomes that are flexible enough to adapt quickly to changes in technology
- No single industry sector or the government will be able to solve the challenges facing the Internet ecosystem, because while the Internet is largely managed by the private sector, governments, civil society, and individuals all have key roles. Successfully addressing cyber threats requires collaborative efforts from across the Internet ecosystem. The ongoing effort to produce the Botnet Report is an example of this collaborative approach in action.
Panel Discussion with Evelyn Remaley
The panel discussion following Remaley’s presentation tackled both baseline questions around the incentives at play in the current IoT ecosystem and the upcoming Botnet Report’s role in addressing the risk of distributed threats, as well as practical questions about where the policy development process goes after the final report is released. Mark Walker moderated the panel discussion between Evelyn Remaley (NTIA), Michael Bergman (Consumer Technology Association), and Tracy L. Lechner (Brownstein Hyatt Farber Schreck, LLP). The panelists discussed the incentives misalignment that keeps a significant number of IoT providers from investing in better device security, including the perception that consumers do not place a significant value on security and that increased security comes at a significant cost (time and/or money). They also discussed the availability of effective security controls and the various industry efforts to drive increased adoption of those controls.
Panel Discussion on Risk Landscape for Enterprises
The final session entitled The Risk Landscape for Enterprises: Attacks, Recovery, Liability, and Compliance covered the cybersecurity threat landscape from the enterprise perspective. This panel was moderated by Blake Reid (University of Colorado Law School; Silicon Flatirons) who lead the discussion with Paul Diamond (CenturyLink), John Diana (LogRhythm, Inc.), Ryan Howe (Webroot, Inc.), and Deborah Shinbein Howitt (Lewis, Bess, Williams & Weese, P.C.). The discussion focused on the challenges enterprises of all sizes face when tackling the rapidly changing cybersecurity risk landscape, including limitations on resources and talent, as well as the task of understanding and complying with the numerous legal obligations coming onto the scene. Much like developing a cybersecurity program, building up the required legal policies begins with identifying the most critical data a business handles (e.g., healthcare information, social security numbers, credit card information) and then creating incident response plans that meet the most stringent obligations in those areas first. The NIST Cybersecurity Framework was highlighted as providing an enterprise with a structured approach to assessing cybersecurity risks and developing a robust cybersecurity program that matches its unique needs.
As CableLabs continues to focus on developing new and innovative security technologies, we must continue to ensure we have a sound understanding of the rapidly evolving cybersecurity policy landscape, both here and abroad. But, just as importantly, policymakers should have a sound understanding of current and developing technologies. Events like this help bridge those gaps in understanding.