Wireless
Wi-Fi: The Unsung Hero of Broadband

Key Points
- More Wi-Fi networks are being deployed to meet the growing need for better broadband connections.
- WFA Passpoint and WBA OpenRoaming have helped expand the public Wi-Fi network footprint.
We hear a lot about 5G/6G mobile and 10G cable these days, but another technology is also helping lead the pack to much less fanfare. It’s a technology that’s as essential as the public utilities you rely on every day. In fact, you’re most likely using it to read this blog post.
Just as you expect your electric, water, sewer or natural gas services to be available without interruption, you likely also depend on your Wi-Fi to be working all the time.
Regardless of the service you use to access the internet (i.e., coax, fiber, wireless, satellite), Wi-Fi is the typical connection to that service. When was the last time you connected a wire to your laptop or had a great experience using your mobile device over the mobile network while inside your home or workplace? The fact is, most of us make use of Wi-Fi when we’re indoors.
Why Wi-Fi? Why Now?
With the introduction of Wi-Fi 6/6E, Wi-Fi 7 and Ultra High Reliability (Future Wi-Fi 8), Wi-Fi is growing to meet and even exceed the growing need for fast, reliable and lower latency broadband connections. It is available basically everywhere you go — work, school, shopping and even while in transit — allowing you to be connected over a high-speed network just about anywhere.
There is an argument that Wi-Fi is not usable or available outside of the home or work. This is rapidly changing as operators, venues, transportation services and even municipalities deploy Wi-Fi networks. It’s true that mobile networks have greater outdoor coverage, but many of the applications in use only require low bandwidth, which is not the case with Wi-Fi.
Evolving Wi-Fi Network Applications
In the car, kids often watch video or play games, which are likely carried over mobile. But now many newer cars on the road have a Wi-Fi hotspot built in. The automotive industry is shifting from mobile connections to Wi-Fi as makers update their onboard software options. Autonomous vehicles and robotics are making use of Wi-Fi, too.
Many mobile carriers are moving to Wi-Fi offload to reduce costs and help meet the demands of broadband traffic. Wi-Fi access points (APs) are now at a price point that almost every home has at least one AP or Wi-Fi extender, with many homes having more than one. In work environments, businesses can quickly deploy a Wi-Fi network on their own or with a third party.
Frameworks for a Wider Wi-Fi Network Footprint
With the addition of WFA Passpoint and WBA OpenRoaming™, the public Wi-Fi network footprint continues to expand. Passpoint allows internet service providers (ISPs) to offer a seamless Wi-Fi connection experience like the mobile connection experience. Passpoint is now included in 3GPP specifications as the named function to assist with mobile devices connecting to Wi-Fi network. OpenRoaming enables access network providers (ANPs) to offer Wi-Fi services to users regardless of their home ISP. This allows providers the ability to offer more locations where subscribers can access Wi-Fi networks. Identity providers (IdPs), such as Google, Samsung and Meta, can also make use of OpenRoaming Wi-Fi network access for their subscribers.
We expect our home utilities to function reliably every day, and now Wi-Fi has become an essential service, supporting our daily activities such as living, learning, working and, of course, playing. For more on Wi-Fi 6/6E, Wi-Fi 7 and Wi-Fi 8, stay up to date here on the CableLabs blog.

Wireless
Enriched Wi-Fi Performance Through Wi-Fi Multimedia

Key Points
- A collaboration between CableLabs and Meta found that Wi-Fi Multimedia (WMM) could improve the performance of voice/video calling applications when it is enabled on an access point.
- Given the positive results from the testing, operators might consider using WMM to ensure the necessary throughput, low latency and managed jitter for time-sensitive applications such as these.
- The details of the testing and results are included in a technical report available for download below.
Network service providers and application developers both work to provide their users with the best possible quality of experience (QoE) for their respective services. Although many segments of the service/application layer of end-to-end networks are out of the operator’s control, the segments between the user’s device and the internet are not.
One such critical and consistent segment within the home network is Wi-Fi — the preferred and most commonly used network access technology in the home. This last link has become synonymous with the overall internet. Ensuring the best throughput and latency of these services/applications will reflect on the user’s experience and therefore determine how good or bad the internet service is.
Not all applications have similar traffic needs with regard to throughput, latency and jitter. One such category of applications is Real Time Communication (RTC), examples of which include voice/video calling applications such as Messenger and online meeting applications such as Zoom and Microsoft Teams. To ensure necessary throughput, low latency and managed jitter for RTCs, providers might consider the use of the Wi-Fi Multimedia (WMM) feature.
Wi-Fi Multimedia in Test Scenarios
WMM has four categories of traffic: Voice (VO), Video (VI), Best Effort (BE) and Background (BG). Traffic within each of the categories is given different priorities. Without WMM enabled, all traffic is treated equally, meaning that web browsing and email exchange, for example, are treated the same as time-sensitive applications such as RTCs.
A collaboration between CableLabs and Meta examined the WMM feature to determine the potential for overall improvements to an RTC application. The results of this testing showed that — with WMM enabled on the access point (AP) — RTC applications had improved quality of video and audio, even with varying traffic-load conditions on the Wi-Fi network. In addition to weathering changing traffic loads, RTC quality was maintained as the RTC device moved over varying distances from the AP.
Testing involved emulating a single-family dwelling using three locations. At each location, the RTC client was placed close to the AP (near), midway from the AP (mid) and at the AP’s serving edge (far). Test scenarios consisted of two types of contention traffic: The first introduced typical traffic as seen in a home setting, representing the use of various home applications, and the second fully loaded the Wi-Fi network with simulated traffic. Throughout the testing, the RTC device was shifted to different static distances from the AP (near, mid, far) and QoE was measured in every case. Testing also included a sweeping test case in which the RTC client was moved from near, mid and far locations (in relation to the AP) and then returned to the near location simulating a person moving within the home (sweep). Tests were conducted in the 2.4 GHz band using a 20 MHz channel, as well as the 5 GHz band using an 80 MHz channel.
The results showed that, with WMM enabled, RTC applications experienced improved performance compared with RTC applications not using WMM. This outcome was consistent over all testing: static at near, mid and far locations, and while moving the device from near to edge and back.
Reporting on WMM Testing Results
The details of the testing and results are available in a technical report, “Impacts of WMM on Wi-Fi — Study of Real-Time Communication Quality and WMM.” CableLabs is eager to take these positive lab results and test them in the field to prove the benefits of WMM in real-world environments. After downloading and reviewing the test reports and results, members are encouraged to contact me if they are interested in participating in trials to prove the benefits in a real-world environment.

Wireless
Finding Solutions to Randomized Wi-Fi MAC Addresses
As Wi-Fi device and OS vendors move to implement Randomized and Changing MAC Address (RCM) to reduce or eliminate the ability to track users and their devices, related functionality costs on the Wi-Fi industry are emerging. This blog will discuss how the industry is enhancing users’ privacy while working to maintain legitimate functions that require a stable means of device identification. It will wrap up by discussing the effects of RCM on beneficial tools and industry efforts to address those impacts through innovation and new technology development.
Functionality Impacts of Wi-Fi MAC Randomization
As privacy has become an increasing priority, addressing unwanted tracking of individuals and devices has become central to enhanced privacy efforts. Device and OS vendors have started to implement RCM to negate this tracking risk for consumers. This shift was previously discussed in an earlier CableLabs blog post titled “MAC Address Randomization: How User Privacy Impacts Wi-Fi And Internet Service Providers.”
When a user’s device is on a Wi-Fi network, the Wi-Fi MAC address is used as part of the transport protocol. Anyone with a Wi-Fi sniffer can identify the specific device and associate it with the user as he or she moves about (e.g., entering and leaving an area). At that point, the malicious entity can use the Wi-Fi MAC address to track the user at future locations based on previously correlating the user’s device to the user. RCM randomizes the MAC address, disabling the correlation between the device and the user because the same MAC address isn’t repeatedly used.
RCM implementations differ based on the device and OS vendor; these range from Wi-Fi sessions, time periods and associated SSIDs (network names), to name a few. Although RCM can help reduce and even potentially eliminate the ability of a third party to track a user, the capability comes at a cost. RCM impairs legitimate functions, features and services that rely on a static, non-randomized MAC address to identify that device. Several examples of functions hindered by RCM include captive portal authorization, parental controls, allow/deny access lists and lawful intercept.
The Wi-Fi Industry’s Solutions
Because of the impairments to legitimate functions that occur based on RCM, the Wi-Fi industry is working to develop alternative methods of identifying devices without exposing the device identity and creating the risk that a user might be tracked. The first step in this process is identifying use cases in which the device identity needs to be known for legitimate purposes. Several Wi-Fi industry organizations—including Institute of Electrical and Electronics Engineers (IEEE), Internet Engineering Task Force (IETF) and Wireless Broadband Alliance (WBA)—are working on identifying and detailing these use cases.
Although each organization is working independently, each also recognizes that cooperation and information exchange are critical to addressing the issue in a timely and unified manner. CableLabs is leading the effort and actively contributing across several organizations to ensure that consumers are protected while functions important to broadband network operators continue to operate. Through the collective support of a Wi-Fi industry composed of operators, device and OS vendors, and other vendors, innovative solutions are being explored and specified to ensure that a balanced solution emerges.
Get Involved
Some vendors are already considering device-identification solutions that don’t require a static MAC address and allow privacy risks to be mitigated without breaking key functionalities. One promising approach, known as fingerprinting, develops a unique device signature through evaluating radio frequency and traffic characterization. Similar solutions are being investigated to identify the presence of individual devices necessary for legitimate features to operate. However, even with these solutions, some may still allow a third party to identify and correlate devices to users, enabling the devices and users to be tracked.
The industry still needs a secure method of identifying devices without hobbling features, functions and services that depend on a static Wi-Fi MAC address while protecting data privacy concerns. To get involved in defining use cases and helping to create the right solution(s), you can join one (or more) of the industry organizations that are addressing RCM.
For more information, please contact Luther Smith (l.smith@cablelabs.com).

Wireless
Bringing Wi-Fi Security to the Next Level
WBA PKI Framework Enables RadSec Connection Security
In 2020, the COVID-19 pandemic nearly eliminated travel. Today, as restrictions are lifted, we’re seeing travel levels increase—particularly locally. Soon, we should all be able to return to the world of far-reaching travel.
Whether for trips across town or journeys around the globe, Wi-Fi accessibility is a critical necessity in the 21st century. Using various Wi-Fi roaming technologies such as Passpoint®, Wireless Broadband Alliance (WBA) WRIX and OpenRoaming™, we can enjoy the Wi-Fi connected broadband experience wherever we go. And as we move about, there are many Wi-Fi networks available to us from various operators; most are secured by some level of security, whether a shared secret, captive portal or Extensible Authentication Protocol (EAP), also known as 802.1x.
Many service providers are moving to EAP for user authentication, a tactic that not only simplifies access to their own Wi-Fi network but also enables a secure roaming experience for their users. To allow users to be authenticated and gain access to roaming Wi-Fi networks, user credentials need to be routed to the home service provider. This interconnection between the roaming partner and the home service provider has typically been over IPSec tunnels. The introduction of RadSec is changing the method of interconnection. RadSec offers a full end-to-end secure path and the ability to use dynamic interconnections.
RadSec interconnection security is based on the mutual exchange of certificates between the two operators, enabling authentication of the operators and encryption of the information exchanged. To standardize these certificates, WBA members (under the leadership of CableLabs) undertook the creation of a solid RadSec PKI framework.
The WBA team led by CableLabs are proud to have completed the PKI framework and have made it available for deployment and use by all members of the WBA, marking the closure of the WBA Roaming Evolution Working Group. The PKI framework includes the PKI Certificate Policy (CP), Trust Root Certificate Authority (CA) agreement, Policy Intermediary CA (I-CA) agreement, Issuing I-CA agreement, End-Entity agreement, Operator Deployment Guidelines and End-Entity Deployment Guidelines.
The completion of the PKI framework is ready to advance and make Wi-Fi roaming simpler. There are several roaming implementations that will benefit from the PKI framework, including specific inter-operators’ roaming deployments, the WBA Wireless Roaming intermediary eXchange (WRiX) and OpenRoaming.
The WBA PKI framework is currently available to WBA members and PKI certificates by Kyrio®, a wholly owned subsidiary of CableLabs. Moving forward, the WBA Roaming Work Group will continue to manage the PKI framework and documentation including the new project, “Profiles & RCOIs Prioritization”.
For more information about the WBA PKI framework contact pmo@wballiance.com and to get your RadSec certificates, contact PKIOPS@kryio.com.

Wireless
WBA OpenRoaming™ to Enable Global Wi-Fi Roaming

On May 28, 2020, the Wireless Broadband Alliance (WBA) announced the launch of OpenRoaming. OpenRoaming is a cloud federation–based framework that will open Wi-Fi roaming to a broad community of Identity Providers (IDPs) and Access Network Providers (ANPs). OpenRoaming is a cyber-secured, seamless connection and automatic RADIUS router all rolled into one global multi-provider ecosystem. The fundamental makeup of OpenRoaming spans multiple technologies: Passpoint, DNS Discovery, RadSec and components of the Wireless Roaming Intermediary eXchange (WRIX).
OpenRoaming works by using Roaming Consortium Identifiers (RCOIs) to allow Passpoint-driven ANP selection. The RCOIs are identified by two major categories, Settlement Free and Settlement, followed by two sets of subcategories. The subcategories define roaming consortium types and service levels. The roaming consortium types span from general consortiums to industry-specific consortiums. Service levels include none, silver and gold, each defining the level of network Quality of Service (QoS) and the rate of reporting QoS information.
Current roaming platforms are based on the use of specific realms, 3GPP network identities or roaming consortiums for the selection of the Wi-Fi networks with static peer-to-peer interconnections over an IPSec tunnel for RADIUS traffic. OpenRoaming, which Figure 1 shows, established ANPs to support multiple consortiums coupled with dynamic RadSec interconnections, eliminating the need for static peer-to-peer interconnections. An additional benefit is the use of RadSec, a RADIUS client/server connection using TLS for security, which not only eliminates the need for an IPSec peer-to-peer tunnel but also encrypts the RADIUS traffic from RADIUS client to RADIUS server, which secures traffic deeper into the providers’ networks.
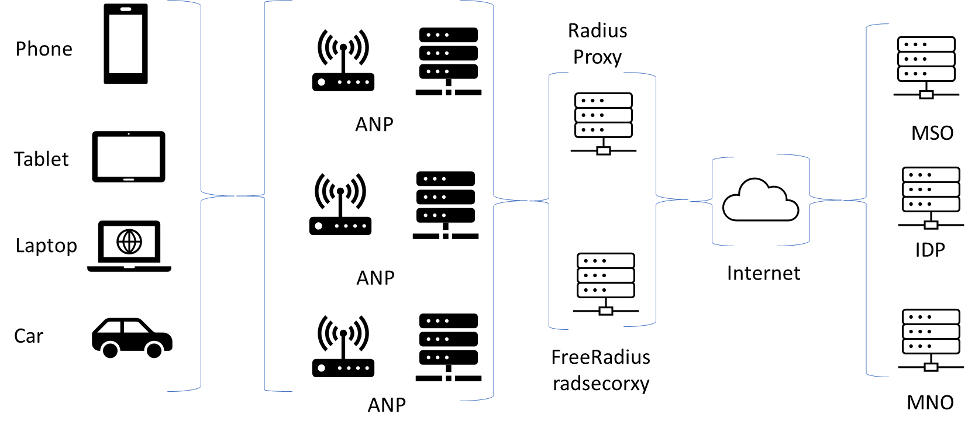
Why OpenRoaming?
OpenRoaming allows the cable industry to easily establish an inter-roaming partnership across the industry while reducing the overhead of a networking setup. With the defined cable industry-specific RCOI, ANPs can be targeted as part of the cable consortium.
OpenRoaming provides users a seamless Wi-Fi connection beyond the subscriber’s home service area, reducing the need to rely on a cellular data connection. Beyond the operators that provide Wi-Fi services, OpenRoaming is a tool that can be used by Mobile Virtual Network Operators (MVNOs) to assist with Wi-Fi connectivity, enabling cellular data to offload. This would broaden the data offload from a local network to a global network.

Wireless
RadSec, Securing RADIUS Message Exchange

With the ever-increasing use of mobile devices for data-rich activities, mobile networks have felt the burden of handling larger amounts of data. To gain relief, mobile operators have turned to offloading data onto Wi-Fi networks that are locally available—not only their own networks but Wi-Fi networks owned by their roaming partners. If the roaming partner’s Wi-Fi network is secured, then the subscriber’s credentials are exchanged between the roaming partner and the home operator, typically over the Internet. These credentials need to be secured while traversing the Internet, and the most common method is to use IPSec secure tunnels. Although IPSec secures and encrypts this critical information over the Internet, IPSec is not without issues and risks.
One issue is that the information is encrypted only from firewall to firewall, leaving the data unencrypted within both operator networks. In addition, setting up IPSec can be cumbersome because of the amount of work typically involved and the number of individuals, which can include the server administrator, network administrator, firewall administrator and security individuals. There’s also the issue of performing key exchanges and testing the connections; the entire process is repeated if either end of the connection needs to be altered, resulting in downtime.
A Solution to These Issues Is RADIUS Security (RadSec)
Although RadSec is still a draft specification within the IEEE (RadSec profile for RADIUS), it’s based on TLS RFC 6614 “Transport Layer Security (TLS) Encryption for RADIUS,” which enables the securing and encrypting of RADIUS messages between the RADIUS client and server. RadSec ensures that all RADIUS messages are secured and encrypted not only when they’re sent over the Internet but also when they’re deeper within each operator’s network, starting with the client and server. Because RadSec is based on TLS, the client and server are mutually authenticated at connection time, ensuring a trusted connection by chaining the certificates to a trusted Root Certificate. By using certificates, the revocation of certificates can be used to eliminate unauthorized connections. In addition, TLS offers encryption of the RADIUS exchange. Encrypting the exchange prevents the exposure of sensitive subscriber information at all points between client and server—within the roaming partner’s network, over the Internet and within the mobile operator’s network—making the entire path secure.
RadSec is flexible and scalable. With RadSec, the client or server IP addresses can be altered without having to reconfigure the secure tunnel settings, as is the case with IPSec. The number of peering clients and servers can also be increased as needed based on operational requirements—without requiring additional work to establish new secure tunnels. This flexibility contributes to RadSec’s scalability. With traditional secure tunnels, if additional roaming partnerships formed, firewalls need to be set up to support the new tunnels. With RadSec, at the most, firewall access control lists (ACLs) would need to be updated to allow traffic from and to the new partner; the same certificate can be used for all roaming partnership connections.
Based on the benefits of RadSec, CableLabs has led the work in Wireless Broadband Alliance (WBA) to introduce RadSec to the WBA Wireless Roaming intermediary eXchange (WRiX).
For more information about RadSec, please contact Luther Smith (l.smith@cablelabs.com).

Reliability
A Better Wi-Fi Experience with Dual Channel Wi-Fi™

At least 15 percent of customer service calls are Wi-Fi related, ranging from poor connections to video playback issues, translating to more than $600 million in annual support costs for the cable industry (in North America alone). As the Wi-Fi industry looks for ways to increase speed, coverage and support for more devices in the Wi-Fi ecosystem, one critical element has been overlooked: the need to have the necessary airtime to send data to all end devices in a timely manner. Even with faster Wi-Fi connections, if there is no available airtime to send the data, the connection is useless. CableLabs realized this shortfall and addressed it with the development of Dual Channel Wi-Fi technology.
What Is Dual Channel Wi-Fi?
Dual Channel Wi-Fi delivers an efficient and more reliable wireless connection.
The wireless networking technology that we commonly refer to as Wi-Fi is based on the 802.11 standard developed by the Institute of Electrical and Electronics Engineers (IEEE). The 802.11 standard, in turn, has its origins in a 1985 ruling by the U.S. Federal Communications Commission (FCC) that made the Industrial Scientific Medical (ISM) unlicensed radio frequency bands available for public use.
Wi-Fi is often referred to as “polite” because it uses a procedure called Listen-Before-Talk (LBT). LBT is a contention-based protocol that requires data-transmitting devices to listen and wait for a given frequency band to be clear before sending data. If the device (access point [AP] or station) does not detect transmissions, it proceeds to send data. If the device does detect transmissions, it waits for a random period of time and listens again for a clear frequency or channel before commencing transmission.
Wi-Fi has become ubiquitous over the years and is the primary method by which we connect devices in the home, at work and in public places to reach the internet. Multiple Wi-Fi devices in a typical broadband home can cause contention for available frequencies. Dual Channel Wi-Fi addresses Wi-Fi congestion issues by providing one or more channels for downstream-only data in addition to the primary bi-directional channel. The primary channel is used for upstream and small downstream packets and the others channel(s) are used for large downstream and time-critical data, like video. By offering operators configurable tools to intelligently redirect Wi-Fi traffic, better air-time utilization is achieved for all traffic, resulting in fewer interruptions and a much better Wi-Fi experience for everyone.
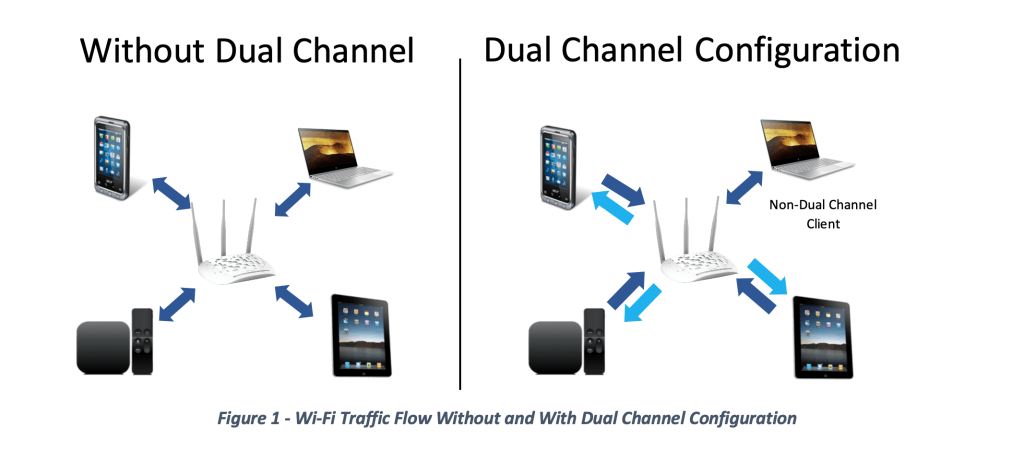
Benefits of Dual-Channel Wi-Fi
Dual Channel Wi-Fi benefits more than just downlink-only clients:
- A better overall multi-user experience: As demonstrated in our performance testing, without Dual Channel Wi-Fi, tests using two standard Wi-Fi channels show issues with video streams, gameplay delays, download buffering and slower throughput to individual devices. By moving data off the standard Wi-Fi channel, it effectively clears traffic from the channel, allowing both the AP and other clients more opportunities to send data.
- A radically improved multi-user experience: By virtually eliminating hesitation and pixilation of video delivery, Dual Channel Wi-Fi enables smooth gameplay without delays and faster overall delivery of data to both Dual Channel Wi-Fi and non-Dual Channel Wi-Fi devices. In our tests, depending on the application download speeds, data transfer speeds increased up to 12 times while airtime efficiency (by reducing the need for retransmissions) increased by 50 percent.
- Reduction of downlink data packet errors and packet retries: The AP’s ability to send data to clients without contention interference has reduced downlink data packet errors and packet retries, resulting in a reduction in uplink retry messages. This, in turn, allows the AP to send more TCP segments at a time, further reducing the amount of uplink traffic.
These improvements in data delivery over the Wi-Fi network as a whole are an example of user experience improvements that can be achieved by technologies that complement the cable industry’s 10G initiative. As the cable industry drives towards faster speeds, lower latency and increased reliability, Dual Channel Wi-Fi helps ensure that those benefits are experienced all the way to end user devices.
Because Dual Channel Wi-Fi is not limited to one downlink-only data channel, deployments in venues such as stadiums, airports or outdoor arenas can also benefit. Dual Channel Wi-Fi’s configurable filters can selectively assign, move or remove devices from individual downlink-only data channels. The mechanism to determine which downlink-only channels that different devices should be assigned is open to vendor development. This ability will allow operators and vendors to perform load balancing across the downlink-only data channels. The result is the management of the network to ensure the best user experience.
Dual Channel Wi-Fi is compatible with all Wi-Fi releases, including Wi-Fi 6. Dual Channel Wi-Fi has been developed and tested on various AP and client platforms. These include RDK-B, RDK-V, Ubuntu, Windows, MacOS and OpenWrt, which was co-implemented by Edgewater Wireless. Both CableLabs and Edgewater Wireless are excited about the opportunity to improve Wi-Fi for users around the world and look forward to working with standards bodies, internet service providers and device manufacturers of video set-tops, streaming devices, laptops, tablets and gaming consoles.
For more information about Dual Channel Wi-Fi, test results and implementation guides, click below.

Labs
Successful OnGo Interoperability Test Event Held at CableLabs

During the week of August 27th CBRS-Alliance members and government representatives gathered in Louisville Colorado at the CableLabs facility for the first CBRS OnGo™ Interoperability Test Event. The attendees consisted of a Spectrum Access System (SAS) Administrator, Citizen Band Service Device (CBSD) vendors, Domain Proxy (DP) vendors, End Unit Device (EUD) vendors and operators and representatives of various government agencies.
CBRS-Alliance is an industry organization focused on driving the development, commercialization and adoption of OnGo™ shared spectrum solutions. The CBRS Alliance enables a robust ecosystem through the management of the OnGo brand, and the OnGo Certification Program. OnGo provides an in-door and out-door LTE network that is cost-effective and can be used for either data offload or private LTE and IOT applications.
The testing covered critical functions of the CBRS ecosystem, “end-to-end” test cases, and operational flexibility. The success of the event shows the maturity of the WinnForum specification and the overall readiness of all parts of the ecosystem for Initial Commercial Deployment (ICD). This event demonstrated the ease that CBSD vendors were able to register on a SAS and become operational. One such example was a CBSD vendor and SAS administrator that had not previously interacted were able to exchange information, register the CBSD and became fully operational all in less than 30 minutes.
While certification testing focuses on protocol testing with test harnesses, this event was conducted as a real-world deployed system. With over 850 scheduled test interactions, as well as several additional unscheduled test scenarios being executed, we observed no equipment failures or unexplained results. The test cases included “end-to-end” scenarios in which EUD attached to operational CBSDs and were able to successfully access and surf the Internet.
“Last week’s Interoperability Test Event was an incredible illustration of the power of collaboration and as a result of this cooperation – across member organizations, industry liaisons and the CBRS Alliance Working Groups – we proved that the OnGo ecosystem will offer tremendous benefits to end users across market verticals,” said Alan Ewing, CBRS Alliance Executive Director. “Notably, this event provided the first ever connection attempt between certain devices and SAS'. The connections were quickly made in each case and underscored the quality of the OnGo specifications and the maturity of vendor implementations.”
In addition to hosting this event, CableLabs through Kyrio (a wholly owned subsidiary of CableLabs) supplied the PKI certificates used during the event which allowed the CBSDs and DPs to quickly switch between the SASs without having to reload new certificates. This greatly reduced the testing time and eliminated issues related to incorrect certificates being used.
As an active member of the CBRS-Alliance, CableLabs continues to contribute to the specification work that the CBRS-Alliance is developing. CableLabs also holds a position of co-lead in the Test and Certification working group which was fundamental input on this Interoperability Test Event.
For more information how to get involved in the OnGo movement please contact the CBRS-Alliance. To learn how the cable industry can benefit from OnGo please contact Luther Smith by clicking below.


