Security
Cybersecurity Improving the Customer Experience


Most of the time businesses view cybersecurity as a burden on their product line or enterprise operations. There is a general acceptance that security is a high-risk area that the businesses cannot ignore but is viewed by many managers and business leaders as not adding value to their bottom line; a cost akin to regulatory compliance. However, by taking this view, leaders may be losing an opportunity. Visionary executives consider cybersecurity as an area that can benefit their business through improving the customer experience.
When a cybersecurity event affects customers, usually it degrades the customer experience. This can happen in a number of ways. For example, a banking customer may not be able to access the bank's website to perform on-line banking. This was the premise for the attacks against US banks that were attributed to Izz ad-Din al-Qassam Cyber Fighters. For ISP subscribers, infected home devices send email spam, are used in Distributed Denial of Service (DDoS) attacks, steal sensitive customer information, and the customer’s data can be held hostage in ransomware attacks. Recent examples include loss of privacy from baby monitors that can be viewed and controlled by strangers outside the home and DVR that were used to take down major services on the Internet.
For cable operators, the most common types of cybersecurity attacks degrade customer video, phone or Internet services. Cable operator owned infrastructure, operator-supplied equipment, or third party purchased equipment can all be adversely impacted. For example, if a customer's computer becomes infected with malware, the customer's Internet experience from that device is degraded along with other devices on the same network. In addition, the infection drives a higher rate of calls to the cable operator's call centers, can increase the number of truck rolls to customer premises due to misdiagnosed problems, and can lead customer dissatisfaction.
This is not to say that ISPs should be primarily responsible for the cybersecurity security of their customers. ISPs have and will continue to play a role in protecting customers, but as a member of the larger Internet ecosystem. The proliferation of insecure Internet of Things (IoT) devices pollutes the Internet with malicious traffic in addition to risking theft of sensitive customer information. Addressing the problem requires the involvement of stakeholders from all across the ecosystem, not just one industry. CableLabs is helping lead the effort of improving the security of IoT devices through the Open Connectivity Foundation (OCF). We are a vocal advocate for strong device security that improves the customer experience for the device and the network ecosystem.
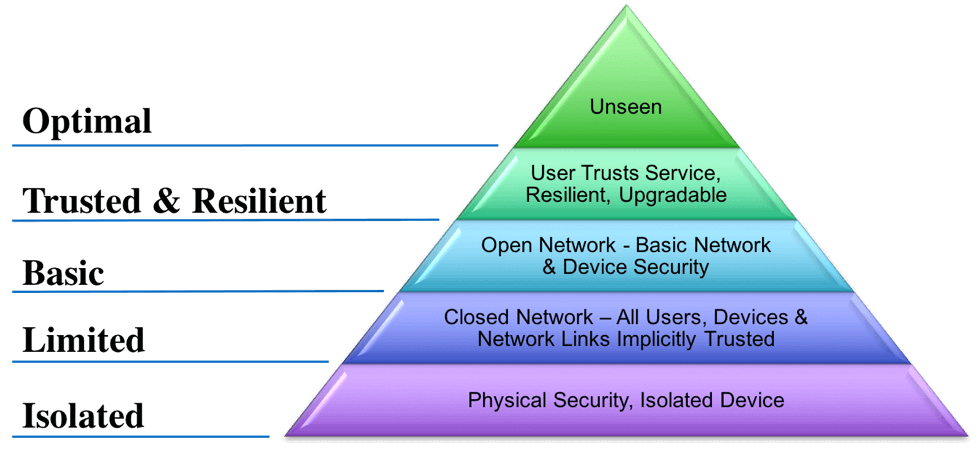
CableLabs has been working on a model to describe different levels of cybersecurity and the impact they have on customer experience. It is based on Maslow's Hierarchy of Needs and is modified from work Microsoft commissioned based on cybersecurity and reaching the full potential of the Internet. In our case, the model describes the user experience that cybersercurity plays on different types of network connected devices.
The model starts at the bottom with isolated devices. It moves up to closed networks and then to basic security on open networks. This “Basic” layer is where most home computers have operated until recently. The "Trusted and Resilient" layer is where good cybersecurity principles are considered in the product design. The device or service is resilient to attacks, upgradable and most importantly, the user has long term trust in the product. Finally, at the “Optimal” top layer, designers of products incorporate strong security controls that provide a more ideal customer experience where the security controls become less intrusive through good design but still provide high levels of protection.
Users should not have to remember passwords as the dominant authentication method. Placing secure PKI certificates in devices provides many benefits. Devices can connect automatically to authorized Wi-Fi access points and adjust to load demands. Device spoofing is dramatically reduced or eliminated. Secure end to end encryption with mutual authentication is facilitated. Software can be automatically upgraded using cryptographically validated downloads with smart defaults for end users for the design life of the product.
In connected homes, residents can centrally manage smart devices, and when the house is sold, the seller can reset the devices to remove their personally identifiable information. Software "keys" to the home can be securely transferred from the seller to the buyer without worry that the seller still has access to the devices or the home. Product designers leverage security to improve the customer experience rather than bolting it on at the end in a cumbersome manner.
Soon, consumers will have tens and hundreds of connected devices in the home and mobile networks. Unfortunately, security issues will likely get worse before they get better due to the large influx of new devices. Work needs to be done quickly to not only mitigate the damaging effects of insecure devices but to dramatically improve the security of these devices. Smart designs and architectures can leverage both good security practices and improve the user experience at the same time.
The cybersecurity system hierarchy is complex, and CableLabs is facilitating discussions with cable operators and other Internet ecosystem players in this space. Please join CableLabs on April 12-13 in NYC at our Inform[ED] Conference to continue this discussion on IoT security.