Wireless
MAC Address Randomization: How User Privacy Impacts Wi-Fi And Internet Service Providers
In the era of mobility, location tracking is a major privacy concern for portable device users. Although a growing number of applications make use of location data, operating systems (OSs) provide the ability to turn off location services provided by the GPS or cellular/Wi-Fi connectivity. Wi-Fi access points, however, can monitor device locations without user consent by means of MAC addresses. As a countermeasure to this privacy threat, OS developers are anonymizing MAC addresses, thereby raising technical concerns among network operators.
Unique MAC Addresses Enable User Privacy Infringement in Wireless Networks
Every Wi-Fi radio has a unique 48-bit identifier called a MAC address that is assigned by the manufacturer. The MAC address is a Layer 2 (L2) address used to identify the source (sender) and the destination (receiver) of frames by most 802 network technologies, including Ethernet, Bluetooth and Wi-Fi.
Back in 2013, the privacy implications of targeted probe requests started to become widely publicized. Several companies were reportedly logging and tracking the addresses of nearby devices in unassociated states. In addition, during the connection to the AP, customers were not notified upfront that their movements would be tracked, and historic location data could be used for marketing purposes or sold to third parties.
MAC Address Randomization Increases Device Anonymity …
In response to these privacy vulnerabilities, most OSs—including Android, iOS, and Windows—began to implement their own variant of MAC address randomization while probing the Wi-Fi network. This probe mode guarantees anonymity until the client gets associated with an AP. IEEE 802.11 also stepped up to specify a similar feature in the IEEE 802.11aq Pre-Association Service Discovery amendment to the 802.11-2016 standard.
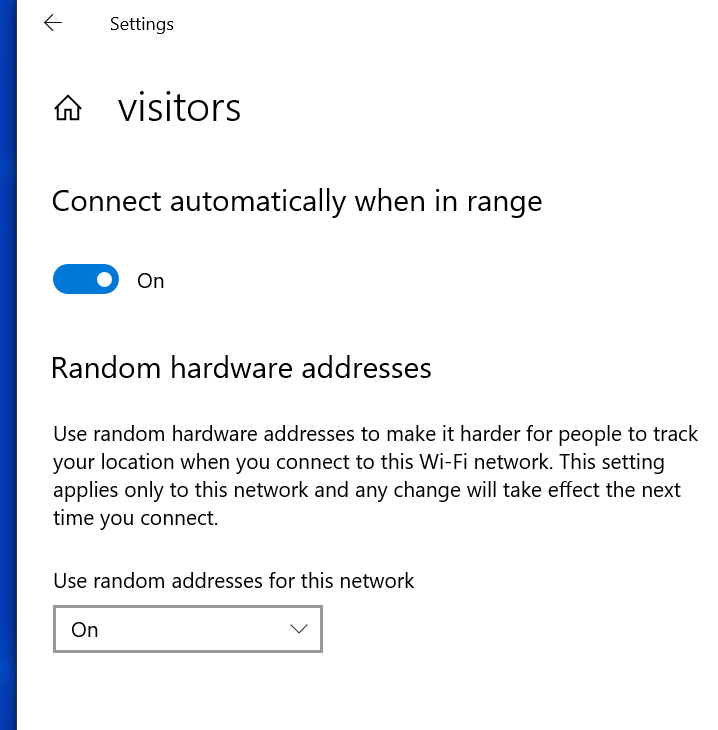
More recently, OSs have started to implement the use of MAC address randomization for device association to the network. The address is kept consistent per network (i.e., Service Set Identifier [SSID]), so the user doesn’t have to authenticate each time it connects to the same SSID. This feature was added to Android P for experimental purposes, whereas Android Q randomizes the MAC address by default, with per-network customization. Windows 10 implements a similar scheme, while iOS 12 supports the probe mode only.
… But Raises Concerns Over Networking Equipment and Services
Although MAC address randomization is evidently a major step toward user privacy, it can have a wide range of repercussions impacting the Wi-Fi network and other related services. The concerns can be classified into two major categories depending on how/where the MAC address is used, the L2 network layer or the system layer.
At Layer 2, MAC address randomization can impact network components: One client may be reported multiple times, and networking equipment might be filled up with outdated MAC addresses. Changing MAC address can also negate the effectiveness of some wireless features. For example, band steering and client steering that optimize client connectivity in a multiple AP environment depend on a unique MAC address for probes and association. To address these concerns, IEEE 802.11 recently formed a Random and Changing MAC Addresses (RCMA) group that is assessing the impact of changing MAC addresses on 802.11 features, for both associated and unassociated device states.
Because the MAC address is a Layer 2 identifier, its usage was not intended for beyond L2 networking. In a recent Liaison Statement to the Wireless Broadband Alliance, the IEEE 802.11 working group “strongly recommends against using any specific MAC address as an identifier for a user or device, outside the scope of the layer 2 communication.” However, due to its ubiquity and, so far, expected uniqueness, the MAC address is widely used for various purposes, such as security, access control and billing. The following are examples of such uses:
- MAC-based access often admits or denies wireless association based on the connecting device’s MAC addresses. This includes authentication methods using the MAC address in lieu of a username and password, Pay Per Use (PPU) passes and short-term complimentary services.
- Some accounting and billing systems use the MAC address as a unique device identifier.
- MAC address filtering is often used to add an extra layer of protection on the network (white/blacklist) and enforce policies such as parental control.
- Monitoring, troubleshooting and analytics of Wi-Fi deployments, including help desks, often rely on MAC addresses as part of the client identity.
- Lawful interception makes use of MAC addresses.
Although no recent public data are available, the use of randomization is expected to increase in the near future as more OSs implement it. The definition of a universal randomization policy would support user privacy while ensuring that Wi-Fi and Internet service providers can take proactive measures to update applications and upgrade networking equipment. This requires the involvement of all stakeholders, including standards bodies, hardware/software manufacturers, service providers and OS developers.
CableLabs is currently addressing this topic in the wireless R&D group. Please contact me if you’re interested in getting involved. To learn more about our work in standards and industry consortia, see our members-only (login required) wireless space.


